Executive Summary
Online piracy is a topic we’ve covered a lot in the past as it remains an increasing problem for companies, artists, and unsuspecting users - one study conducted recently found that the number of visits to piracy sites in 2022 grew by more than 20% compared to 2021. Online piracy also continues to be utilized by cyber attackers who leverage it to distribute malware to users.
ReasonLabs researchers have discovered numerous malicious web extensions that are being delivered to users through a Trojan installer. The installer is hidden in thousands of torrent files claiming to be prominent video games such as Grand Theft Auto (GTA), Assassins Creed, and more. Our RAV EDR product flagged suspicious activities on a large number of users, which led to an investigation whereby we uncovered the widespread malware campaigns.
The malicious installers we identified forcibly install one of at least three different malicious web extensions for Google Chrome or Edge, claiming to be Virtual Private Networks (VPN). Google has removed all of the malicious extensions identified in this blog from the Chrome Web Store. The most prominent extension is called netPlus and had over 1 million users, while the other two extensions, netSave andnetWin, had nearly 500K combined installations.
What The Installer Does
The installer is delivered mainly from torrent downloads claiming to be prominent video games such as Assassins Creed, GTA, The Sims 4, and Heroes 3, and constantly presents itself as setup.exe, followed by tagging itself “by Igruha”. We have come across more than 1000 different torrent files that deliver the same setup file. The most common signer name of these files is “SPICE & WOK LIMITED.” Most of the installer files are about 60MB in size, but some are even 100MB or more. The installer unpacks one of the three malicious extension files and forcefully installs it to the user’s browser.
The installer is installing the web extension through the registry key of “SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings\”. This method is more sophisticated and less commonly used than the “--load-extension” command line argument or “ForceInstall” registry key force extension loading methods. This method changes browser files via Secure Preferences to complete the installation and register the extension without the user’s knowledge or need for approval.
The installer then installs two different extensions - one extension for Chrome (netSave) and a different one for Edge (netPlus).
What The Fake VPN Extensions Do
The JavaScript code of the extensions is massive and contains over 20,000 lines of code. It’s unclear and extremely difficult to understand the code’s full activity but we were able to verify that it’s not just a fake VPN but also runs a cashback activity hack.
To ensure its success, the extension will disable all other cashback extensions from the infected browsers, while also implementing a real VPN UI with minor functionalities to keep up the facade. All of the extensions are in Russian and seemingly targeted at Russian-speaking users. They share the same code and screens in the Google Web Store; however, the developer names, titles, and descriptions differ slightly.
Each extension has several user reviews stating that the extension was installed onto their browser without their knowledge. In addition, the installer comes with chromium-based files, probably for additional actions of web surfing, but it requires further research.
The netPlus extension was also present on the Chrome store with the same extension ID - chiiididmecdffakklhibjpjkbfiaeni; however, it was removed from the store in May of 2022. The code of both extensions has a lot of similarities, although with slight changes. Both the name, description, screenshots, and summary are the same, and they both are involved with cashback and coupons.
The current version of the netPlus extension communicates with a C2 server, announces installation, and gets configuration data from the server. The configuration data is a long JSON (JavaScript Object Notation) with long lists of extension IDs and domains.
The netPlus extension does implement the UI and activity of a functioning VPN but considering all of the other actions, we do not believe that it is a legitimate VPN security extension and therefore should be removed from the Chrome Web Store.
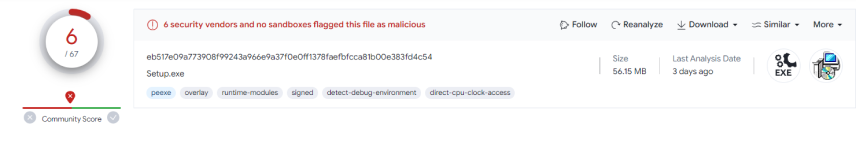
The installers that deliver these extensions are barely marked on VirusTotal by other antivirus providers, and this campaign has gone under the radar for quite a long period of time.
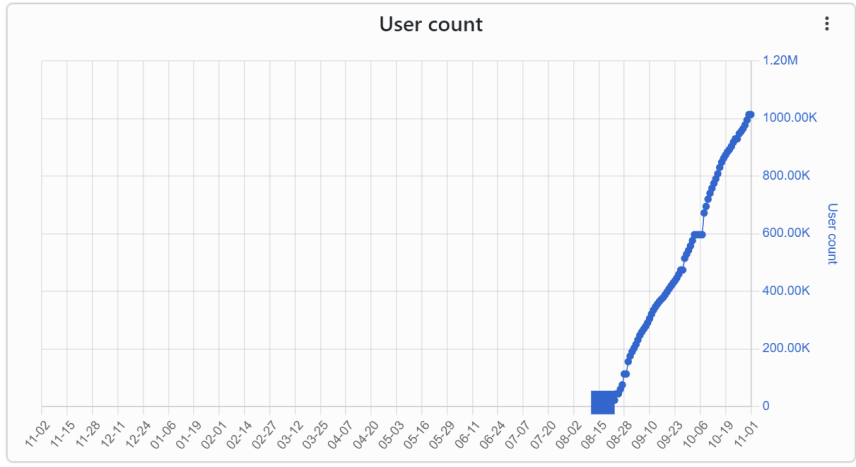
User Count and Location
By using data from Chrome-Stats, we can see that in only two months the extension has grown from zero to 1M users. The extension’s user base is not natural and is installed without the user’s knowledge.
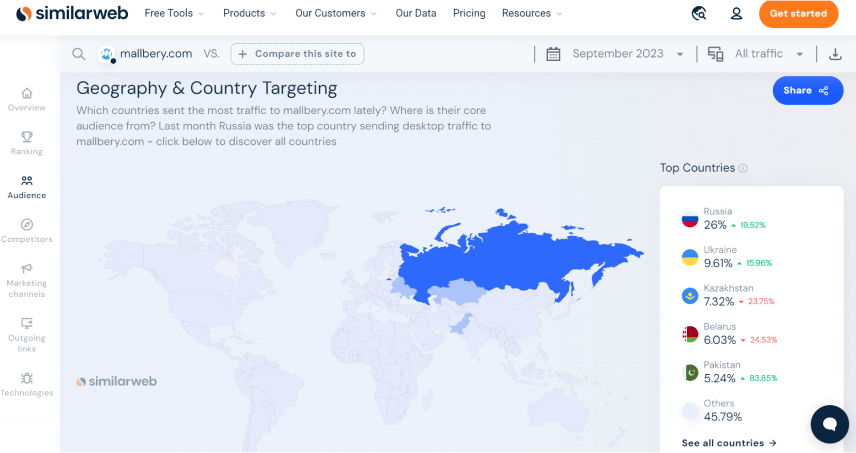
Since the three web extensions are in Russian, it is safe to assume that they are targeted at Russian-speaking users. Using data derived from ReasonLabs users, we were able to identify tens of thousands of users infected with the Trojan across Russia, Ukraine, Kazakhstan, Moldova, and more - countries with many Russian speakers.
One of the domains we found the extensions communicating with is Mallbery[.]com. If we inspect traffic data for the website from Similarweb, we can also see the majority of users come from Russia, Ukraine, Kazakhstan, Belarus, and more.
Technical Overview
Installer analysis
We found thousands of SHA-1s, but let’s take 32d3e031ca2d98f7719f1a4cee95b2d0fc846b8b as an example. The installer is an electron app, usually 60MB and above in size. Inside are modules and scripts that currently seem to be placed there as a distraction. The real interesting code is found packed inside the app.asar. After extracting the app.asar contents, we discover that the main.js code loads fork-entry.js, where some interesting bits await us.
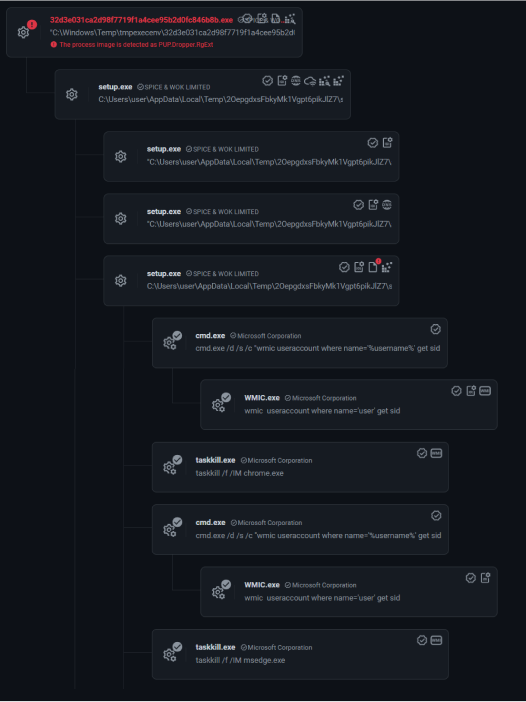
Upon execution, the installer unpacks itself in a randomly-named folder underC:\Users\user\AppData\Local\Temp, contacts “t-oapp[.]ru” and “dns[.]google”, executes WMI queries to get the user SID, and kills all active browser processes.
In addition, it will unpack an “e.zip” zip file which includes all of the extension’s files into the user’s browser directory, both to Chrome and to Edge. To ensure the extension will load onto the browser, the installer will add a registry value into“SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings\”.
Part of the operations required to make it work is to change contents inside the browser files, such as:
C:\Users\user\AppData\Local\Temp\ext-RkN7G9\extension\_metadata\computed_hashes.json
C:\Users\user\AppData\Local\Temp\ext-RkN7G9\extension\_metadata\verified_contents.json
Doing so is a relatively new way to force a web extension installation on a user without needing approval.
Files that are dropped to disk:
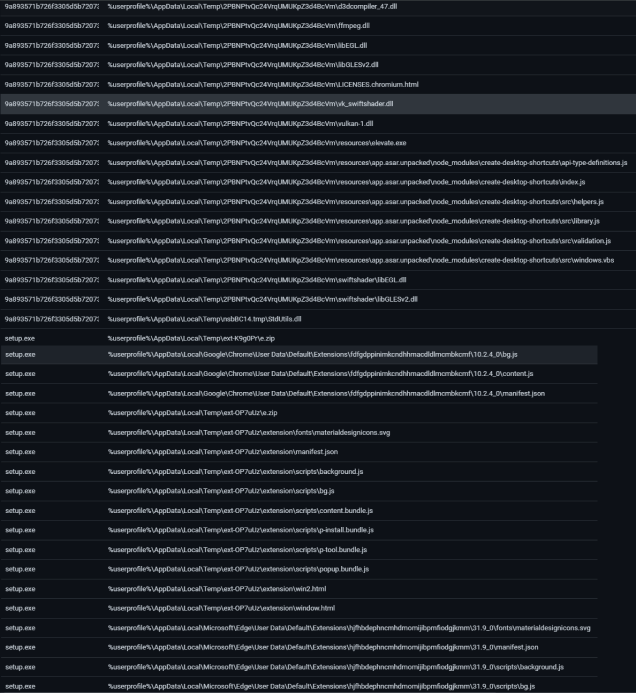
Inside fork-entry.js we find the core elements of the installer. The behavioral process tree from above is part of the code inside this script.
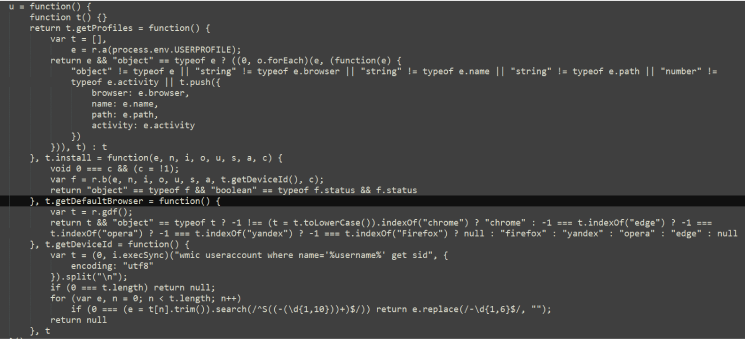
Besides that, the installer checks for antivirus products installed on the machine.
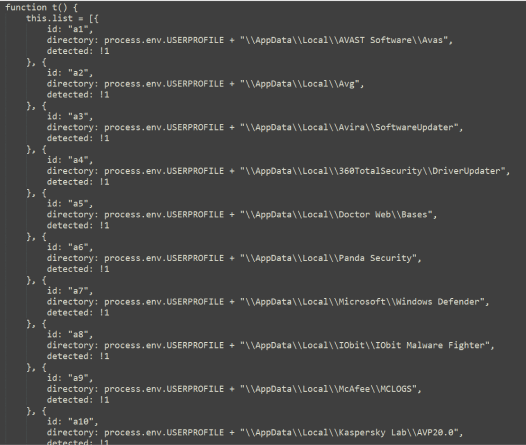
C&C Requests
Upon execution, setup.exe connects to the C2 server (t-oapp[.]ru) and submits information about the infected host. Later it will receive configuration and binaries. It contacts the server with a unique identifier to the station, first announcing that it was installed on the machine
https[://]t-oapp[.]ru/api/game-launcher/iv-18-e3dcc5f211f4ee60666ffa38073d2b6e308076d9/event/launch
The post request is empty, containing only empty brackets
7B 7D {}Immediately after that, a request for config is sent:
https://t-oapp.ru/api/game-launcher/iv-18-e3dcc5f211f4ee60666ffa38073d2b6e308076d9/config
The installer receives back the following:
DataBackgroundUrl:https[://]app[.]my-panel[.]ru/images/game_launcher_backgrounds/f9814faa-d2ce-4351-aab1-1b7f857f5f47.pngDataConfigFile:\AppData\Local\Programs\game1.iniDataHideMode:trueDataName:GTA San AndreasDataRemoveOnInstall:DataUpdateUrl:nullresult:true
A request is made likely sending information about installed extensions:
https://t-oapp.ru/api/game-launcher/iv-18-e3dcc5f211f4ee60666ffa38073d2b6e308076d9/exts/list?country=en-US
Finally, another important request is for data:
https[:/]/t-oapp[.]ru/api/game-launcher/iv-18-e3dcc5f211f4ee60666ffa38073d2b6e308076d9/exts/data?country=en-US
In response to this post request, we received the extension ID to install and a binary file. The file is sent in a base64 format. After decoding it, we received a zip file (PK header) which contains extension-related files:
{“result”:true,“data”: {
“id”:“iv-86-d0657285c2bd96b2ec7ceb98fbf7abc281665cc5”, “eId”:“
<b>hjfhbdephncmhdmomijibpmfiodgjkmm</b>
”,“eIsCustom”:false,“eIsFixedId”:true,“eFile”:“UEsDBAoAAAAAAPGzC1cAAAAAAAAAAAAAAAAKAAAAZXh0ZW5zaW9uL1BLAwQUAAgACADxswtXAAAAAAAAAAAAAAAAEQAAAGV4dGVuc2lvbi1lZC5qc29u3VbdctpGFH4VV70zDiBEMHDRGYHBKAYb7BBM3IxGiEVakHbl3RUgezLTJBftTGf6Cn2FpNPMJG2avIJ4o54VEKBmOr3uDWjP356z5+c794plCzxFZoCYjznHlHClfK9YAVbKNyvmU2ugHCmWZzGfw4dN6QQj+eVbxHKQj4iAQ8DoPIJ\/LigDKnwJayClZmhwiW5DxKXUENlgx5J3niOxoXOb4UBg4oAMHY3giBBRXhwpaB542MbCdCkYAJ++D7NZ…
Extension Analysis
ExtensionID: hjfhbdephncmhdmomijibpmfiodgjkmm [source]
As mentioned earlier, the extension has a similar name, description, and structure to a previous extension that was taken down from the Chrome Store in May of 2022.
Manifest File
The extension disguises itself as a VPN called “netPlus: бесперебойный доступ к сайтам!”, with a description of “netPlus: Получите доступ к вашим любимым сайтам!”, and sets the homepage URL to be “homepage_url”: “https://netplus-vpn[.]ru/”, activates background.js script, and has permissions to all_urls.
It also has permissions to access all of the following: “tabs”, “storage”, “proxy”, “webRequest”, “webRequestBlocking”, “declarativeNetRequest”, “scripting”, “alarms”, “cookies”, “activeTab”, “management”, and “offscreen”.
These permissions allow the extensions to interrupt the user’s surfing activity and alter their web requests. The extensions hijack permissions to any open tabs, as well as the browser’s storage, enabling the storage of continuous activity. By also hijacking management permissions, the extensions can manipulate other installed extensions by listing and disabling them.
The permission also allows the malicious extension to launch previously installed apps. Although scarcely used, one of the most interesting permissions it invokes is the Offscreen permission. The Offscreen API lets the extension run scripts that interact with the current DOM in a hidden way, without opening a new window or interrupting the user. The permission is used in the background.js script, where the function ye() calls the method to load win2.html, which has one line to call a different script called bg.js into each tab
The installer adds extension IDs on the following registry key:
SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings\
Value name: hjfhbdephncmhdmomijibpmfiodgjkmm
Value: 45C19…..8F6EF6B
This operation is a relatively new (since 2020) abusive way to add an extension to the user’s browser without their knowledge. The initial functionality is intended for legitimate software, but threat actors have discovered how to leverage it for malicious activity together with editing the Secure Preferences of the browser to register the extension. What’s also notable is that in some setups the installer unpacks extension files to the user’s Extensions folder:(%userprofile%\AppData\Local\Microsoft\Edge\UserData\Default\Extensions\ hjfhbdephncmhdmomijibpmfiodgjkmm\).
Fake VPN Extension Activity
The extension seemingly sleeps for five minutes after installation. After five minutes, it calls to initialize the functions, which start its activity. As mentioned earlier, the extension does seem to contain certain VPN options - when clicking on the extension icon, it is possible to “start” the VPN, which displays a fake IP in the Netherlands.
The extension also offers a paid subscription for 150 Russian Rubles. It seems that it processes the subscription via the “TradeMC” website, which is used for gaming monetization. It’s possible that by using this platform, the attacker can draw money untracked.
Network communication has been made to its home address:
https[:/]/netplus-vpn[.]ru/api/v2/extensions/config
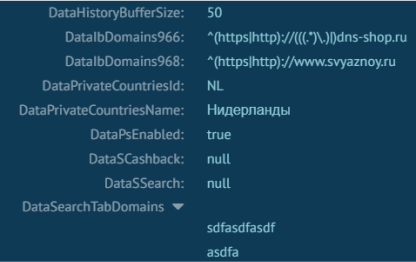
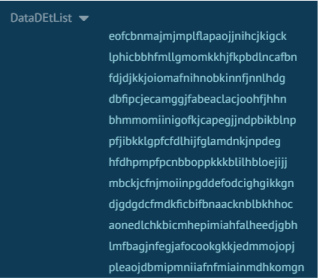
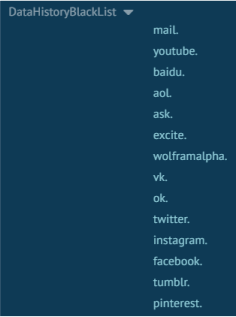
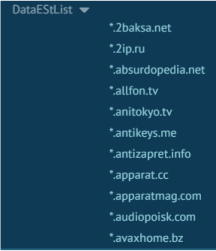
The response to this request provides a long configuration that consists of three long lists of extension IDs, domains, and blacklist URLs:
https[://]netplus-vpn[.]ru/api/v2/extensions/proxy/enable
DataCountryCode:NLDataCountryName:НидерландыDataHost:ehumpq7rv3v5bvr7[.]freemyip[.]comDataPassword:nullDataPort:443DataType:1DataUsername:nullResult:true
Checking the extension from the long list of extension IDs reveals some extensions that deal with coupons, cashback, and online shopping deals. We assume that the extension probably wants to disable any existing extension that could interfere with its cashback activity.
In total, the list has over 100 IDs. For example, such extensions include:
- Eofcbnmajmjmplflapaojjnihcjkigck: Avast SafePrice | Comparison, deals, coupons
- Mbckjcfnjmoiinpgddefodcighgikkgn: AVG SafePrice | Comparison, deals, coupons
- Bmnlcjabgnpnenekpadlanbbkooimhnj: Honey: Automatic Coupons & Rewards
- Lphicbbhfmllgmomkkhjfkpbdlncafbn: Cashback service LetyShops
- Dbfipcjecamggjfabeaclacjoohfjhhn: Cash Back Service Megabonus
- Pfjibkklgpfcfdlhijfglamdnkjnpdeg: AliRadar Shopping Assistant
- Djgdgdcfmdkficbifbnaacknblbkhhoc: Yandex.Market Adviser
- Lmfbagjnfegjafocookgkkjedmmojopj: ChinaHelper - Shop assistant in a Chinese store
- Bhmmomiinigofkjcapegjjndpbikblnp: WOT: Website Security & Safety Checker
- Hfdhpmpfpcnbboppkkkblilhbloejijj: Backit Plugin (“Get cashback for every order in AliExpress, ASOS, Banggood, GearBest, Hotels.com, and 220 Volt stores with Backit plugin”)
Some extensions from the list no longer exist on the Chrome store, but from data available online, we can see that their description and names support cashback activity, for example Iehhgmkphdjocnjjobeoccffiiclcmli: Kopikot, which was a Chrome extension that makes online shopping with cashback easier.
During execution in the lab environment, we installed some of the extensions on Chrome and Edge to see what would happen with them. As hypothesized, after the malicious extension was installed, it deleted all of the previously installed extensions that existed.
Other Extensions
During our file analysis, other extensions were found on various other installers that carried the same signer name and the same execution behavior items. Those extensions can also be found using the Chrome-Stats advanced search tool by searching in the “Full Summary” field of the extension for a string that contains “*-vpn.ru”. This is possible because the author listed a support email with the extension name that’s linked to “-vpn.ru” in all the other extensions.
Indicators Of Compromise
Extension IDs:
- Hjfhbdephncmhdmomijibpmfiodgjkmm (netPlus)
- Ipjbhjmcbgmdjfiichbgbmpmgonokpkb (netSave)
- Gandigjpilmchbomlpmfogigbjapofnc (netWin)
- Fdfgdppinimkcndhhmacdldlmcmbkcmf (saveVPN)
- Anacglcdpkfbbimecdffhhglnonejpec (Savemaktic)
- Fajafkhgbcekjfffgnpbbjhdhimgffec (Previous version of Mallberry)
SHA-1s (Setup.exe):
- 32d3e031ca2d98f7719f1a4cee95b2d0fc846b8b
- 87d4f3c815154b963bf84395e543ba57ee1b99d9
- 5cf0bfd320bb3c5780a8aecc8463702858613e70
- 9f8d9bd326f8f93c3fda8aef7942d2bae9ef0fc3
- B0cd0092a504e281ed1591ea8554ede3829a9470
- b260c92a915abe887a8d37ff1528ca3dcacd78c9
- b0cd0092a504e281ed1591ea8554ede3829a9470
- 9a893571b726f3305d5b7207317169e1976d11a2
- ca379bc09fccc5abd0c3794f8e32b51712e75093
- bfaeab7f0303501c5e40d9d8fa3c8700e8d94638
- 9f45ed7c615fe656211fb5fd515b5df0faa31518
- 833d5945dbdab024da6248a32cb3b5758ce490f4
- d8b00934b5a30c2b15e0a761d4dbac10d89cc836
- d3226b0af40311abc2506db4dc05e01416ff8107
- 06fe5e4d2ed1892bb58e551dc144d7dad2230e50
- 9b2de5ee838f4880a84c230b6503b3052271b147
- 47ae21212f023d8a0e7f3fb8a23f8bf58e5ace71
- 64528913496dfc93a4d33dbcf6dfcea18dfb5e4d
- 1c0a364d9c746ab96e832de5ea9f912936e4a454
- 6690a6e886ebaeab887ecced7bd86c121d4d779f
Signer Names:
- SPICE & WOK LIMITED
- DEVELOPMENT ACTION LTD
Network Activity (Domains Contacted):
- Collector-...[.]px-cloud.net/api/v2?
- T-oapp[.]ru
- Netplus-vpn[.]ru
- Netsave-vpn[.]ru
- Savematik[.]com
- trademc[.]org
- Mallbery[.]com
- 188.114.96.7:443
How Home Users Can Protect Themselves
Users can take several measures to protect themselves from cyber threats associated with piracy:
- Use Legal Sources: Opt for legal and legitimate sources to access content. Use authorized streaming services, purchase software from official stores, and buy games, music, and movies from recognized platforms.
- Install Antivirus and Antimalware Software: Ensure you have reputable antivirus and antimalware software installed on your devices, such as RAV Endpoint Protection and RAV Online Security. These programs can detect and prevent malicious software that often comes bundled with pirated content.
- Be Cautious of Suspicious Websites: Avoid visiting websites known for hosting pirated content, as these sites are often rife with malware. Exercise caution while browsing the internet and be wary of sites offering free or unauthorized content.
- Use VPNs: If you’re accessing content from less reputable sources, consider using a VPN like RAV VPN, which is available for Windows, Android, and iOS. VPNs encrypt your internet connection, providing an extra layer of security and anonymity, making it harder for cybercriminals to track your online activities.
- Avoid Clicking on Unknown Links or Pop-ups: Be cautious of clicking on links or pop-ups associated with pirated content. These can lead to malicious websites or initiate the download of harmful software onto your device.
- Enable Two-Factor Authentication (2FA): Use strong, unique passwords for all your accounts and enable two-factor authentication where possible. This provides an extra layer of security, making it more difficult for unauthorized individuals to access your accounts.
By following these guidelines and adopting best practices for online security, users can significantly reduce their exposure to cyber threats associated with piracy.
















