Executive Summary
Today’s world consists of home users who spend countless hours connected online each day. One commonality that joins most consumers is a lack of sufficient cybersecurity with the ability to protect their devices and identities. Many legacy consumer-focused antivirus providers have out-of-date technology and customers of their products must replace them with next-generation antivirus solutions.
ReasonLabs has developed a powerful endpoint protection tool known as Online Security - a web extension with over 9,000,000 users from across the world, accessible on Google Chrome and Microsoft Edge. It protects users by blocking malicious cookies and trackers, provides identity protection services with dark web monitoring, scans for threats, and much more.
In this report, researchers from ReasonLabs’ Threat Intelligence Center detail findings from data derived during May - July 2023, from free and premium users of the Online Security web extension. The report highlights the most common threats found and what home users can do to protect themselves.
Global Spotlight
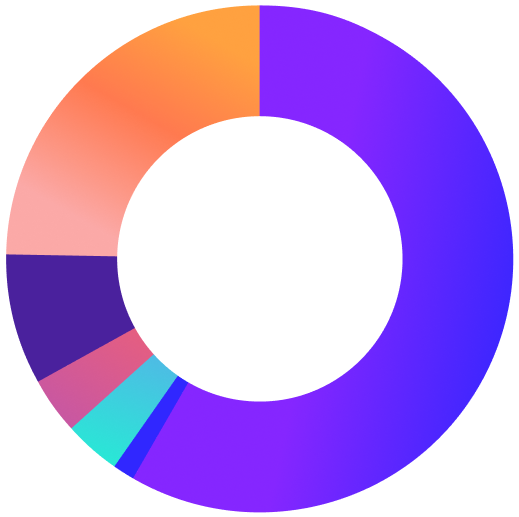
In our 2023 State of Consumer Cybersecurity report, we detailed that Trojans, a type of malware, was the top threat detection from 2022. That trend seems to be continuing globally well into 2023 for a host of reasons, as malware made up more than 58% of all detections from May - July 2023.
Phishing followed with almost 25% of global browser-originated detections, which comes as no surprise as phishing remains the top attack vector affecting home users. Adware, pirated software and content, and crypto mining round out the top five global web threats detected over the summer of 2023.
We will dive deeper into these threats in later sections. For now, we will spotlight the United States to analyze what the top detections were and offer some reasons as to why those detections were most prevalent.
U.S. Highlights
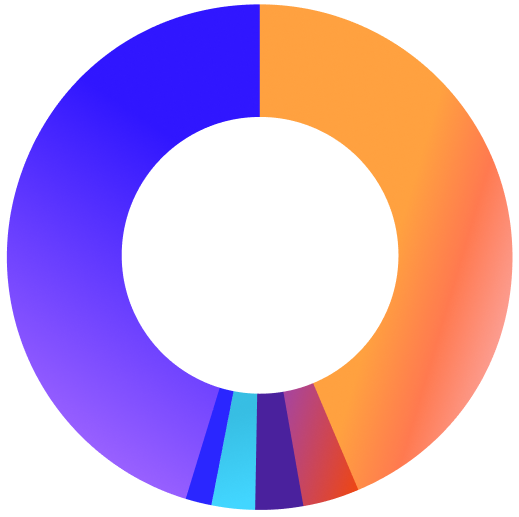
The U.S. data compared to the global data shows some similarities and some glaring differences. Malware is also the top website threat affecting home users, however, phishing detections are almost twice the amount found in the global data.
We also see a notable inclusion of ransomware detections found in U.S. data, which we do not see in global data. Finally, we see that adware and pirated software and content in the U.S. are both not as prevalent compared to the global data. Clearly, phishing attacks are the attack vector of choice for bad actors looking to harm U.S. users.
Top Five Threats Plaguing Home Users
Phishing
Phishing is a cybercrime technique used by malicious actors to deceive individuals and trick them into revealing sensitive information, such as usernames, passwords, credit card details, or other personal and financial data. Overall, it is the top vector for distributing malware, which we have detailed greatly in the past, including in our 2023 State of Consumer Cybersecurityreport.
Below we highlighted various countries across the world to show just how prevalent phishing attacks against home users are. The graph shows the amount of phishing attacks detected compared to the overall detections made.

The most glaring data points to the United States, Russia, and Ukraine. Cybercriminals attacking users in those countries favor phishing attacks, as nearly 50% of all detections made were phishing. Concerning Russia and Ukraine specifically, phishing attacks that lead to threats such as Trojans, ransomware, and more, seem to be the cyberwarfare weapon of choice.
Phishing attacks can have serious consequences, leading to identity theft, financial losses, unauthorized access to online accounts, and other forms of cybercrime. Phishing attacks commonly occur through emails, but they can also take place via other channels like SMS messages, social media DMs, or phone calls. Attackers typically pose as legitimate entities, such as banks, government agencies, online services, or reputable companies, in an attempt to gain the trust of the recipient.
There are several common phishing tactics:
- Email Phishing: The attacker sends an email that appears to be from a legitimate source, often mimicking the branding, logos, and email format of a well-known company. The email usually contains a sense of urgency or fear to prompt the recipient into taking immediate action, such as clicking on a link or providing sensitive information.
- Spear Phishing: A targeted form of phishing where the attacker customizes the attack for a specific individual or organization. The phishing message may reference the recipient’s name, job title, or other personal information to appear more convincing.
- Pharming: In this method, the attackers compromise DNS (Domain Name System) servers or manipulate the victim’s host file to redirect them to fake websites, which appear legitimate, but are designed to collect their information.
To protect against phishing, users should be cautious when interacting with unsolicited emails or messages, verify the legitimacy of websites by checking for secure connections (https://), and enable two-factor authentication (2FA) where possible to add an extra layer of security to online accounts. Users should also leverage a reliable password manager to ensure frequent changes of passwords with strong secure ones.
Malware
Malware, a combination of “malicious” and “software,” is a broad term that refers to any malicious software designed to harm, exploit, or gain unauthorized access to computer systems, networks, or devices. Malware is often created by cyber criminals with the intent of causing damage, stealing sensitive information, disrupting computer operations, or generating illicit profits. There are various types of malware, each serving different purposes that are widely distributed all over the world.
Malware can enter a system through various vectors, including malicious email attachments, infected software downloads, compromised websites, and social engineering techniques. To protect against malware, it’s essential to use reputable antivirus and anti-malware software e.g. RAV Endpoint Protection, keep operating systems and applications up to date, exercise caution when downloading files or clicking on links, and avoid interacting with suspicious emails or messages. Regular data backups are also recommended to mitigate the impact of potential ransomware attacks.
Adware
Adware, short for “advertising-supported software,” can be broken down into two categories: software that drives ads outside of its scope or nefarious adware that induces harm. The latter of the two typically contains malware that can deliver unwanted advertisements onto a device, hijack a computer’s settings, such as search manners, and display potentially dangerous ads, which may unfurl into different types of malicious software.
Adware can be distributed through malicious websites or email attachments sent to unsuspecting users. When installed, adware can sometimes have the ability to collect personal information about a user, for example, their browsing history, preferences, or other online activities.
To protect against adware, it is essential to exercise caution when downloading and installing software. Using a reputable antivirus and anti-malware program like RAV Endpoint Protection or a DNS content filtering service like Safer Web, which can detect and remove adware infections, is critical.
Pirated Software & Content
Sites hosting pirated software and content that include malicious links and downloads were another top detection by Online Security. Pirated content is associated with the distribution of malware as cybercriminals take advantage of the demand for free content to spread malicious software. ReasonLabs researchers made this clear in their recent film piracy report that detailed illegal downloads of movies nominated at the 95th Academy Awards.
Piracy has serious consequences for content creators and copyright holders. It leads to financial losses, hinders innovation and creativity, and undermines the incentives for artists, developers, and content creators to continue producing new and original works.
To support content creators and respect intellectual property rights, it is crucial to obtain and use software and digital content from legitimate sources that have the appropriate licenses and permissions to distribute the material. Using pirated software or content not only violates the law but also exposes users to various risks and potential legal actions.
Cryptojacking
Cryptojacking is a form of cyber attack in which a hacker uses someone else’s computer or device to mine cryptocurrencies without their knowledge or consent. Cryptocurrencies like Bitcoin and Ethereum are created through a process called mining, which involves solving complex mathematical problems using computational power. Miners are rewarded with newly created coins for their efforts.
Mining can be a resource-intensive process, requiring significant computing power and electricity. To avoid the costs associated with mining, some hackers employ malicious software to infect computers, smartphones, or other connected devices and use their computational resources for mining without the owner’s awareness. In 2021, ReasonLabs researchers discovered a novel crypto miner threat being distributed in pirated copies of the Spider-Man: No Way Home movie.
Since cryptojacking often doesn’t cause immediate harm to the device, users might not realize they are victims. However, it can lead to several issues such as reduced device performance, overheating or hardware damage, and increased electricity bills. To protect against cryptojacking, users should take precautions like keeping their software and security tools updated, using next-generation antivirus software like RAV EDR, and being cautious about downloading software or visiting untrustworthy websites.
How Home Users Can Protect Themselves
Protecting yourself from cyber threats is essential in today’s digital age. Endpoint security tools such as RAV Endpoint Protection, RAV VPN, Safer Web, and Online Security from ReasonLabs are all programs that are must-haves for home users. Continued education is also paramount - users must be made aware of the latest threats to learn how to protect themselves. Here are some practical steps that home users can take to enhance their cybersecurity:
- Use Strong and Unique Passwords: Create strong, complex passwords for your online accounts, and avoid using the same password across multiple sites.
- Enable Two-Factor Authentication (2FA): Whenever possible, enable two-factor authentication for your online accounts.
- Keep Software Updated: Regularly update your operating system, web browsers, antivirus software, and other applications to ensure you have the latest security patches.
- Be Cautious of Emails and Messages: Be wary of unsolicited phishing emails, attachments, or links.
- Secure Your Wi-Fi Network: Change the default password on your Wi-Fi router and use strong encryption.
- Backup Your Data: Regularly backup your important files and data to an external drive or a cloud storage service.
- Stay Informed: Follow reputable sources such as cybersecurity blogs, news outlets, and government websites.
- Be Cautious on Social Media: Be mindful of the information you share on social media to avoid oversharing personal details that could be used by criminals.
- Be Skeptical of Tech Support Calls: If someone claiming to be from tech support contacts you, be cautious as legitimate companies usually don’t call users unsolicited.
- Educate Yourself and Your Family: Teach your family members about cybersecurity best practices and encourage them to follow similar steps to protect their devices.
Remember that while these steps can significantly reduce your risk, no system is completely immune to cyber threats. Staying vigilant and practicing good cybersecurity habits is an ongoing effort.
















