In part one, we learned about Javascript as a malware and we started to understand how obfuscation works and how we can start the process of deobfuscation by using beautification to make the Javascript code readable.
2. Garbage Code
So the first layer of obfuscation, as we’ve seen, usually starts with format obfuscation. Next, attackers want to make things harder in case we beautify the code, so for that, they’ll add some garbage code.
Garbage code has no real purpose; it doesn’t affect the code itself in any way. The whole idea of garbage code is just to make things harder to track and to confuse the researcher.
Let’s see an example of garbage code:
– In this example, we see really simple and easy code to read.
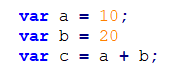
– The code after removing all the Garbage code:
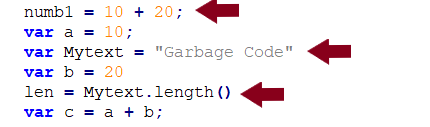
As we can see, the garbage code doesn’t do anything; it just gives a feeling of complexity. You’re probably asking yourself how we can identify this code if we have a lot of Javascript code. The solution is to search for variables and code that are only used once.
Let’s continue with our code from the previous article and see what the garbage code is and remove it:
– The actual code after beautification:
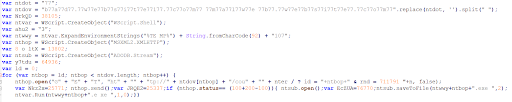
– The code after removing all the Garbage code:

As we can see in the picture above, we were able to make the code shorter and to clean it up a little bit so that we can work on analyzing only the relevant code.
Another type of garbage code is linked garbage code., This type of obfuscation creates linked variables in order to keep things hard to track. When we come across this type of code obfuscation, we use a different way to beat it. We have to follow the code and try to clean the variables and understand what is going on.
Here is a quick example that can help you understand:
– Some nice and short Javascript code:
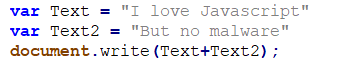
– Linked garbage code:
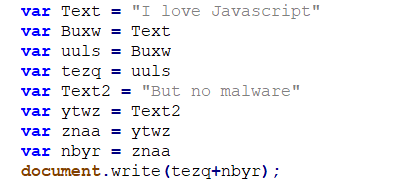
In this example, the code is easy to follow because it’s pretty short, but in some cases, the code could be extremely difficult and time consuming to understand.
Hope you learned something new. Keep it up… until next time.
















