Executive Summary
In 2022, the cybersecurity world is no stranger to phishing attacks, credit card scams, virus distribution, and identity theft. They’re ongoing on a daily basis - and we’ve almost reached the point where we think we’ve seen it all. However, ReasonLabs has just uncovered potentially one of the largest fraudulent online credit card schemes active today.
This significant and widespread global credit card scheme appears to have been operating since 2019. We estimate it has amassed tens of millions of dollars in fraud from tens of thousands of families and individuals. We estimate it is operated by a crime syndicate and found evidence that it originated in Russia. The scam seems to abuse several security brands, such as McAfee and ReasonLabs, to execute fraudulent credit card charges. The infrastructure is built on top of Amazon Web Services and uses GoDaddy to circulate hundreds of domains.
The fraudster’s strategy includes operating a massive fake network of dating and adult websites with functional customer support capabilities. Once the sites are live, the scammers coerce payment providers to gain the ability to accept credit card payments. At this point, the fraudsters search the darknet and acquire thousands of stolen credit cards and charge them to their fake website’s services.
The following report will break down how this elaborate scheme has been operating in three integral stages and offer possible ways for consumers to protect themselves to combat such schemes in the future.
Stage 1: Webpage Creation
Dating Sites
The fraudster group operating this scam has most likely been using proxy people to create a number of fake dating websites. These websites are functional, yet they do not receive real traffic and are very hard locate on Google. However, using our own RAV Managed EDR tool, we received an indication that led our research team to uncover roughly 200 websites all belonging to the same owner:
Domains
Since the operation has been active since 2019, some of these links are only historically related; therefore, we are not publishing the full list as many of the websites have already been taken down. Additionally, some of these domains refer to adult affiliate links, domain parking, or to specific adult cam websites.
As you can see below, many of the sites utilize the same design template and the same user flow:
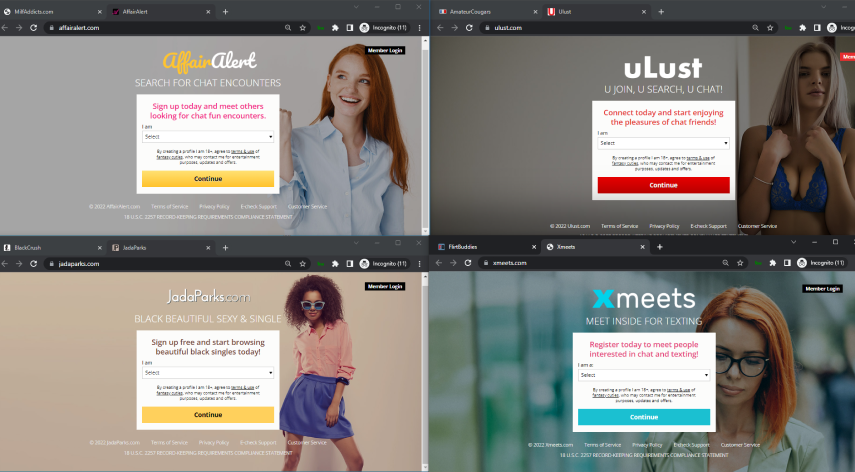
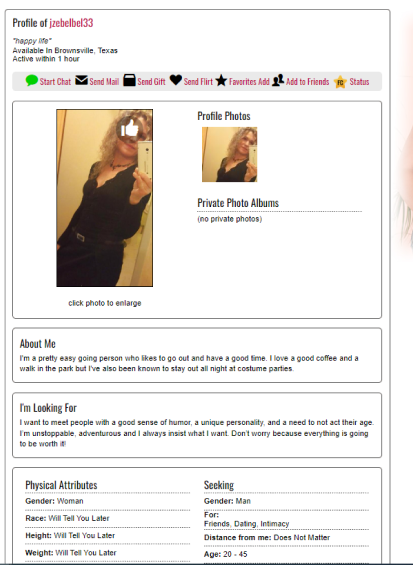
After our researchers registered on these sites, it became clear that they actually contain very few dating profiles - and each one has very limited personal details:
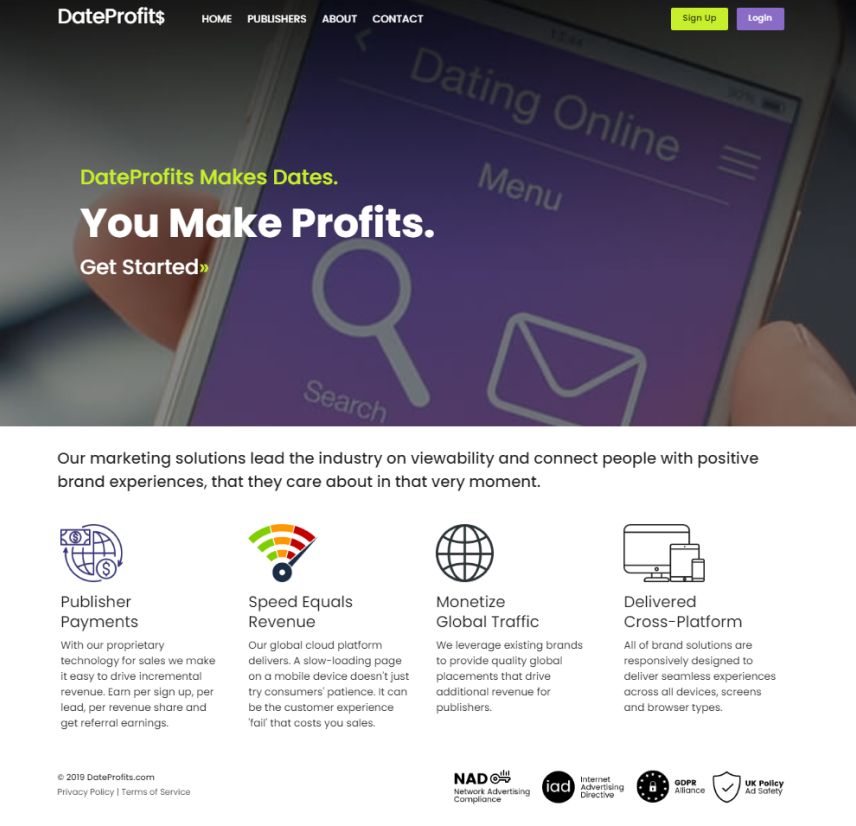
All of the websites refer to https://dateprofits.com/ as an affiliate management program, which is also a fake website:
Dating Sites Characteristics
Most of the websites have barely any traffic, according to https://similarweb.com. However, some do contain traffic, so we compared these sites to similar legitimate ones from the same category.
Our understanding is that the website https://affairalert.com/ is one of the main websites in this scam. Here is the traffic breakdown:

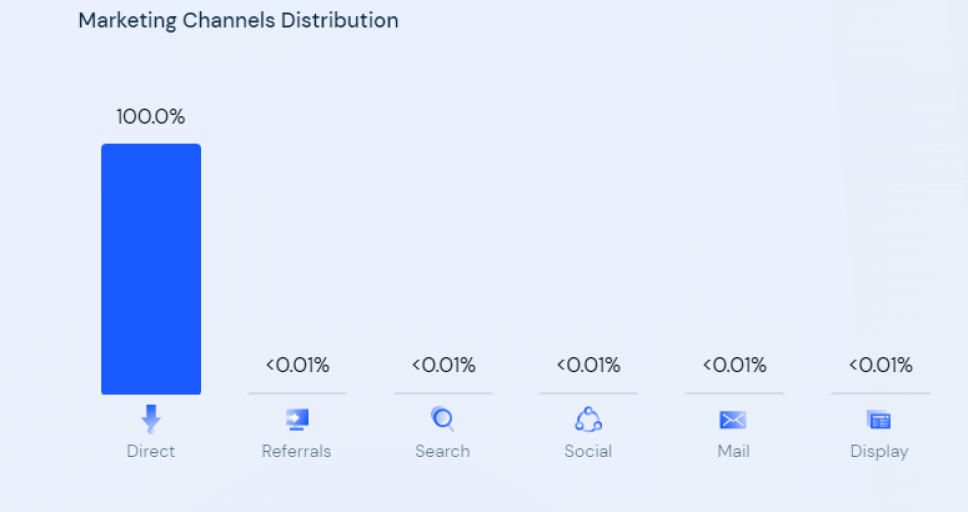
They have just 34K unique monthly visitors, and yet they have a strangely outstanding performance with exactly 11 pages viewed per visitor, and 13 minutes averaged visit time. Even more unusually, at the time of capturing this screenshot, the site had 100% direct traffic.
Here’s how the traffic distribution looks on a legitimate site in the same category of dating:
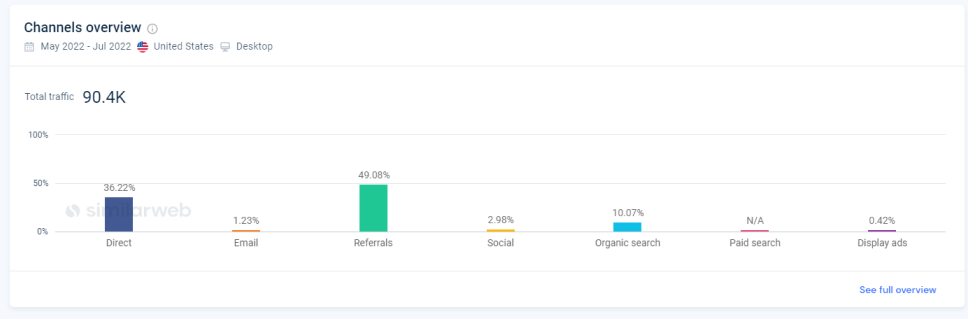
The geography of the scam website’s ‘unique visitors’ is also unique - more than 95% of the traffic is coming from the US.
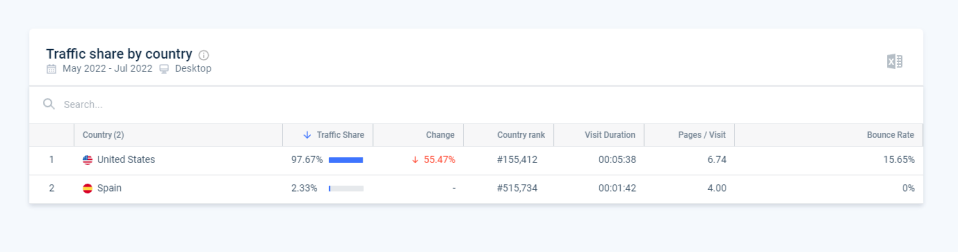
Compared to a legitimate website in the same category, we see that despite the main target market, there is a very long tail of other countries. This is a by-product of the internet being global, and this pattern will be observed on almost every website in the world:
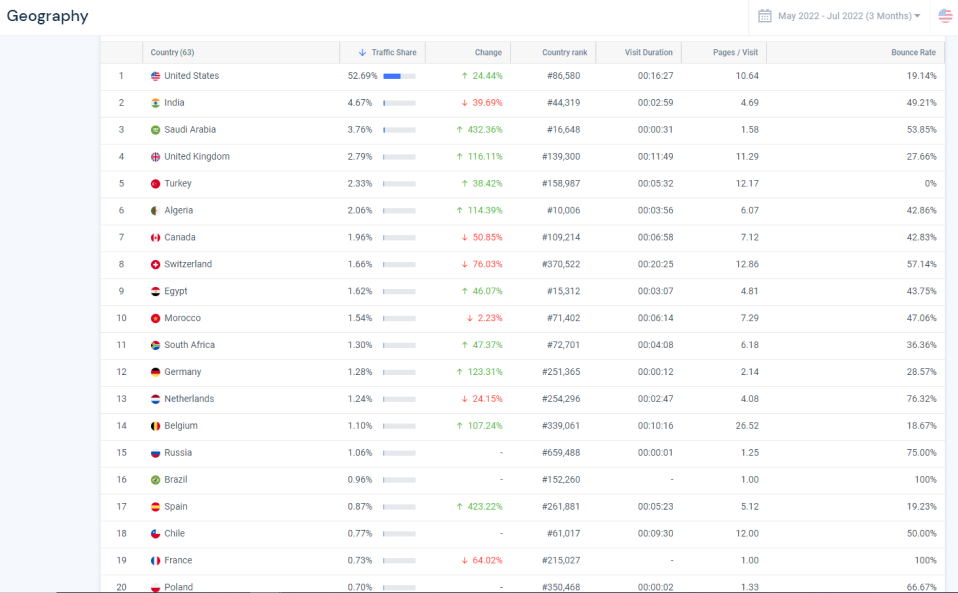
To summarize these findings: We have observed that 100% of the users are entering the site by typing the URL in the address bar, and visiting exactly 11 pages. Also, virtually all of the users are from the US only, despite its being a publicly available website.
Customer Support Sites
In addition to these dating websites, the fraudsters also created 75 different customer support-focused websites. The names of the customer support sites differ from the dating site names in order to masquerade the charge under an amorphic entity, which is stated as a privacy feature for the users on the billing page.
Some of the names have also been crafted to imitate major globally recognized brands seemingly to try and fool consumers once the charge shows up on their monthly bills. These are just some of the websites scraped from the payment pages, including the names that will appear on the credit card statements of the users:
Websitehttp://ZBMFEE[.]COMhttp://yisapp[.]COMhttp://WESTFEE[.]COMhttp://TwoFee[.]COMhttp://TOVABILL[.]COMhttp://TJXFEE[.]COMhttp://texxbill[.]COMhttp://TecroPay[.]COMhttp://SYNFEE[.]COMhttp://swxhelp[.]COMhttp://SURPLUSFEE[.]COMhttp://stebill[.]COMhttp://SECURECARTE[.]COMhttp://Safeonic[.]COMhttp://RokFee[.]COMhttp://RocoFee[.]COMhttp://REDZOFEE[.]COMhttp://Reddfee[.]COMhttp://RADIFEE[.]COMhttp://PRVTRUST[.]COMhttp://PRVFEE[.]COMhttp://PIXEBILL[.]COMhttp://PEAKBILL[.]COMhttp://PAYECLIK[.]COMhttp://PALOBILL[.]COMhttp://PAKFEE[.]COMhttp://OPTBILL[.]COMhttp://OLYMBILL[.]COMhttp://NOBELFEE[.]COMhttp://Netifee[.]COMhttp://MTCHPAY[.]COMhttp://MOBEBILL[.]COMhttp://micofee[.]COMhttp://MEDEFEE[.]COMhttp://MaxiFee[.]COMhttp://LeveBill[.]COMhttp://JETTFEE[.]COMhttp://ITEKBILL[.]COMhttp://irobill[.]COMhttp://INTECBILL[.]COMhttp://INETFEE[.]COMhttp://IDATABILLhttp://IBILLSTATS[.]COMhttp://hzatek[.]COMhttp://HEZABILL[.]COMhttp://GUARDBILLER[.]COMhttp://gteztech[.]COMhttp://GOTOFEE[.]COMhttp://GIGACLIK[.]COMhttp://EZCHRGE[.]COMhttp://EVOFEE[.]COMhttp://ESTARFEE[.]COMhttp://EPALFEE[.]COMhttp://ENNZTECH[.]COMhttp://EEZFEE[.]COMhttp://DTGPAY[.]COMhttp://DTAFORM[.]COMhttp://CryoFee[.]COMhttp://ClasBill[.]COMhttp://cerufee[.]COMhttp://CEBEFEE[.]COMhttp://BYTEFEE[.]COMhttp://bqibill[.]COMhttp://bpobill[.]COMhttp://BBTFEE[.]COMhttp://ayobill[.]COMhttp://AXPFEE[.]COMhttp://AWXCARD[.]COMhttp://ARGOSBILL[.]COMhttp://AresFee[.]COMhttp://APPCHARG[.]COMhttp://ABILLPRO[.]COMhttp://ABAFEE[.]COM
Phone Number833-67408571-888-4227865866-9481758866-9873545833-7017010844-36908011-855-2086186833-61442181-833-4116628844-7424861877-92603391-855-2700935866-9900373866-4593111833-2849998833-8390149855-6807139844-928-0328833-3120920833-3152591855-6162018855-6184915855-5102266877-2120460833-9041460844-9990277855-6570333833-3810787844-6060059866-4489780844-6141968833-4990254833-7518965833-4592159855-5565127855-7253315844-8440988866-63584081-888-86793418333001918855-6721663877-6666384877-80907271-855-2584921833-9010051833-39805091-855-2687496844-8530370833-7320717855-6602388877-6036967877-3783432877-4010468888-7511679877-3803633866-4520606844-5750983855-7201131833-30918711-877-4644580833-8908227833-43205151-888-6063640855-612-2812855-96415451-888-7784709833-9081539855-6201653844-8664456844-50710758773457270877-7363393877-5334198
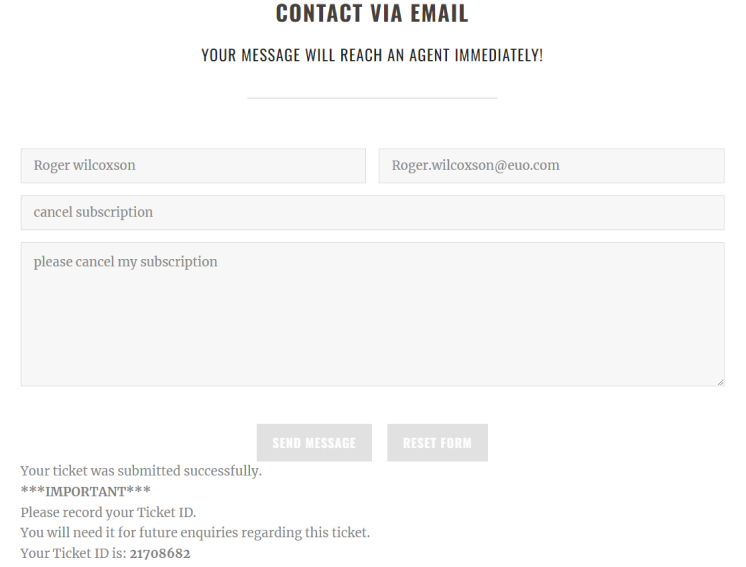
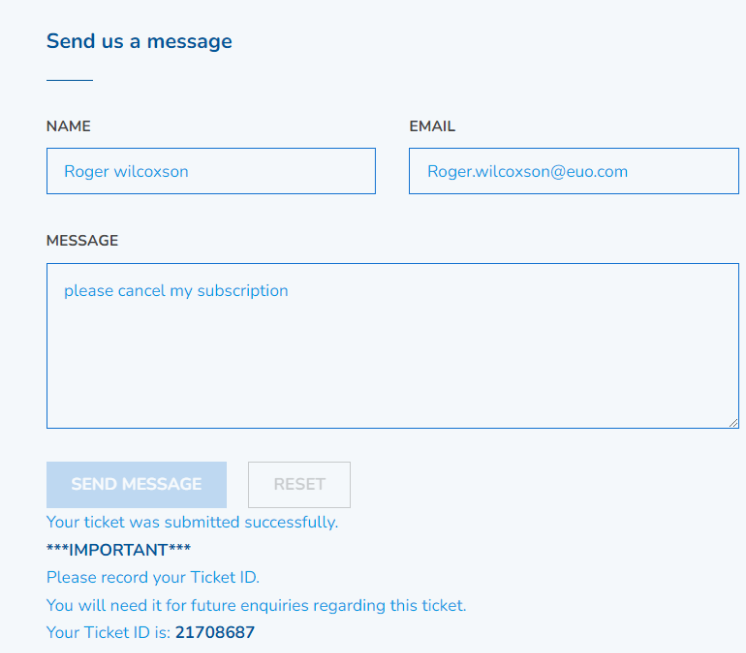
All the websites have exactly the same structure - the organization name in the header, followed by the number of the call center and a form to contact their support:

Customer Support Sites Characteristics
All of the 75 customer support websites have exactly the same HTML structure, using the exact same comments:
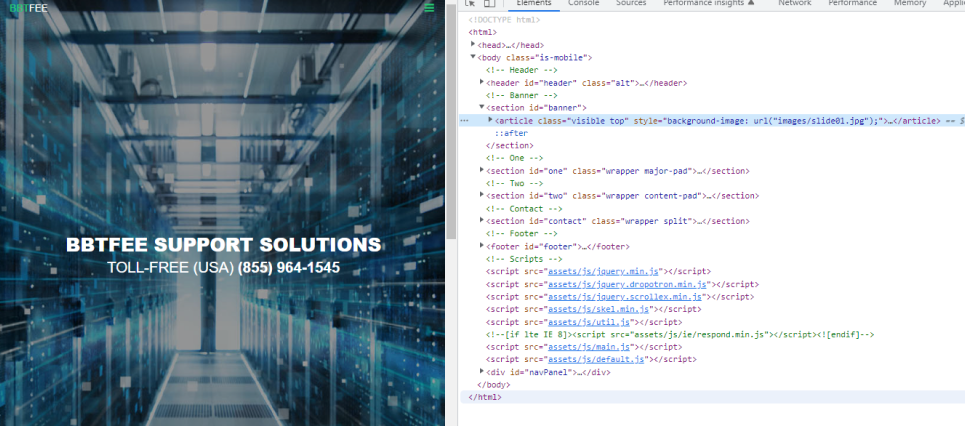
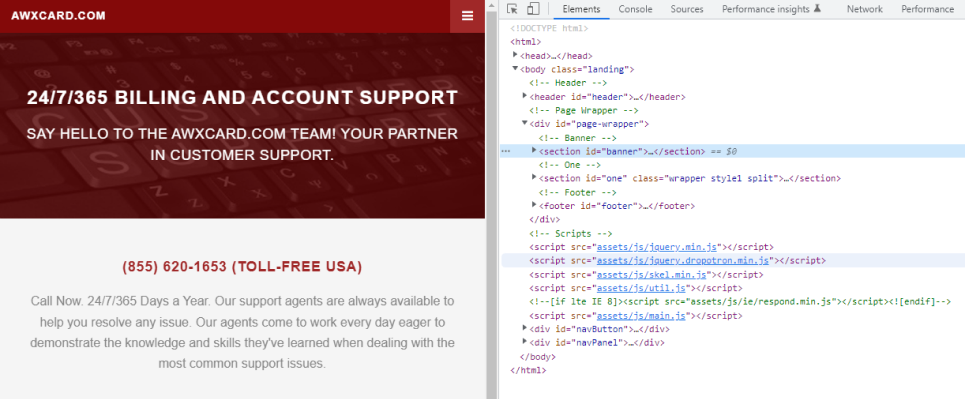
All contact forms are integrated with the https://livehelpnow.net/ service:
All 75 websites are using the same JavaScript, also imported in the same order:
Skel.min.js:
3Util.js:
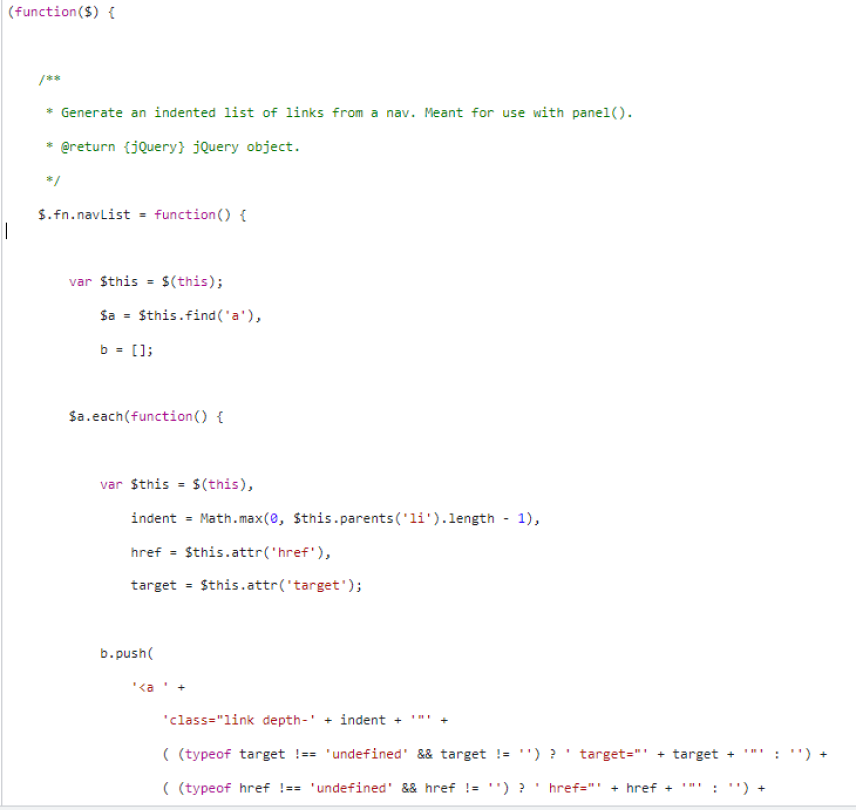
Some of the websites contain ‘disallow all’ in Robots.txt. The scammers do this so their sites do not become indexed on search engines nor tested by any other type of automated crawlers.
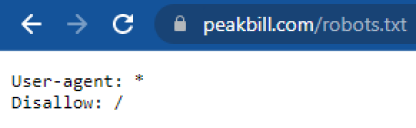
At the bottom of each webpage, images are always used that contain the ‘physical addresses of the companies instead of using basic text. This technique is commonly used in order to avoid indexing the addresses on search engines:
Stage 2: Payment Processing
Payment Acquirers
After the fraudsters create the dating and customer support sites, they must gain the ability to bill ‘customer’ credit cards. This is not an easy task because businesses such as adult sites are usually classified as ‘high risk’ by payment processors. A business typically receives a ‘high risk’ designation because they are characterized by having a high percentage of chargebacks, even when they aren’t used in instances of fraudulent activity.
The fraudsters applied each individual customer service website for payment processing in order to distribute the chargebacks between many websites rather than just one. This would ensure that their payment processing capabilities will not be revoked once one site reaches the agreed rate of chargebacks, or refunds, which is divided by the number of legit transactions. The fraudsters probably justify the huge volume of transactions to the payment processors due to the fact that they have over 200 different dating websites under their operation. Also, the high chargeback rate can be explained by the nature of the industry.
One key detail the payment provider likely looks into is if a customer support line exists (in case a customer requires a chargeback). In this case, all of the 75 support sites have a fully integrated customer support chat that operates 24/7, managed by the company https://livehelpnow.net, which we believe to be a legitimate support center provider.
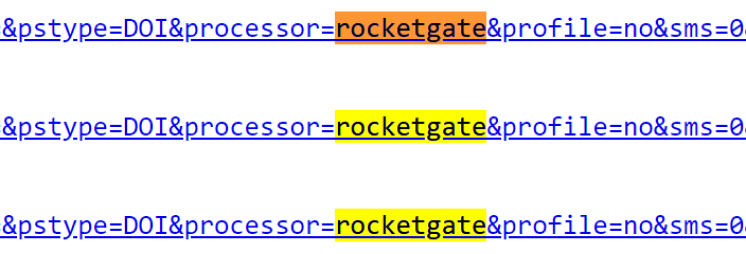
The payment processor seems to be https://rocketgate.com as found inside the source code of the purchase pages on the dating sites:
Credit Card Dumps
While the fraudulent sites are securing payment processing capabilities, the fraudsters seem to have searched the darknet to purchase thousands of lists containing stolen credit card information, also known as CC dumps. CC dumps on the darknet are extremely prevalent, with recent findings by Cybersixgill showing that more than 4.5 million stolen payment cards were up for sale on the darknet during H1 2022.
In this particular credit card scam, the credit cards are mostly derived from the US as the websites are registered in the US. However, we did come across sites in French, so we can assume the scammers managed to acquire stolen credit card data from France or other French-speaking locations as well.
Even on the clearnet, the hard part will be finding a valid supplier, but this can be overcome by purchasing several dumps from several vendors until a valid one is found. Once the fraudsters have been approved by the payment processor and have acquired huge bulks of stolen credit cards, they can execute the third stage.
Stage 3: Executing The Credit Card Scam
Once all the prep work is complete, the fraudsters seem to begin charging the stolen credit cards, either by using an API, or manually. Users are subscribed to monthly recurring payments that look very similar to a generic subscription from any service provider. In case a credit limit is reached, they will reduce the amount charged.
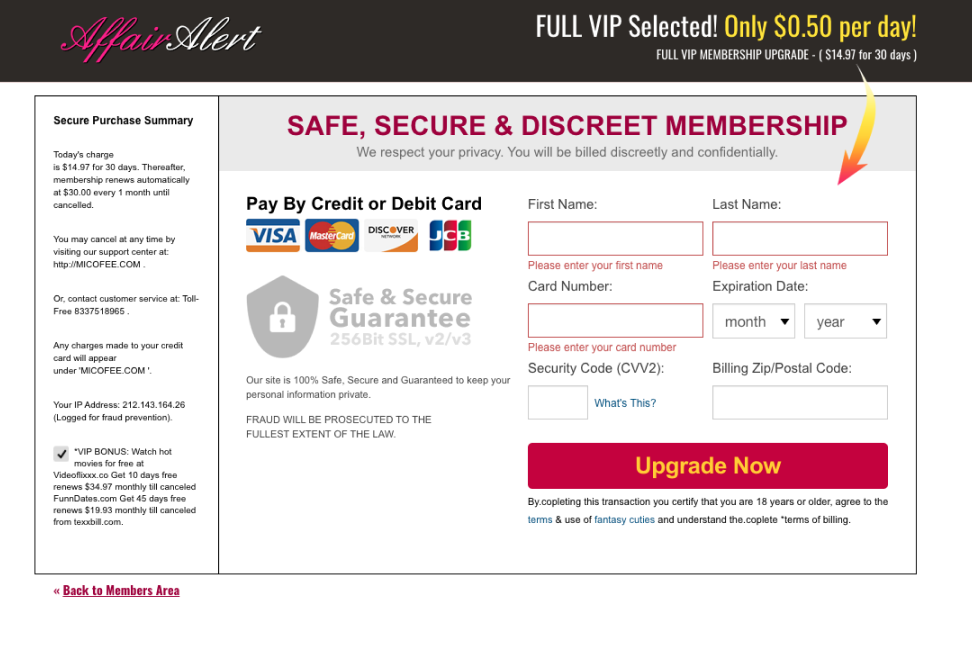
Below is a screenshot of the payment page on https://affairalert.com/:
In a common online credit card fraud scheme, we usually observe a pattern of test transactions which, if passed, are followed by bigger transactions. This goes on until the anti-fraud system of the issuer blocks the card - the idea is to maximize the cash-out, usually by buying goods that can easily be sold.
In order to avoid anti-fraud detection on the issuer’s side, they will usually take the following steps:
- Use recurring payments that tend to be less suspicious.
- Charge only a relatively small amount, very similar to any other subscription service.
- Refrain from performing any test transactions before the main charge.
While signing the agreement with a payment processor, the business agrees upon the cash-out policy. Usually, a policy dictates that the payment can only be withdrawn after the end of the month (Net), but in high-risk industries like online dating and pornography, the processing period can be Net+30. In this type of scheme, it’s very important for the fraudsters to negotiate good payment conditions with the payment providers because their charging abilities will be revoked as soon as they reach their chargeback rate.
In order to stay under the chargeback rate each month, they will do the following:
- Charge small amounts that are not suspicious to the individual.
- Use generic names so individuals won’t be aware of what this charge is about.
- Use a website where a user can request to cancel their subscription. The fraudsters will actually cancel and charge the customer back in order to minimize the issuer’s requests for chargeback, hence lowering the chargeback rate.
- Offer a toll-free number for individuals to call and cancel the transaction, making the site seem more legitimate in comparison to other similar schemes that won’t use any customer-facing component.
On the billing page, the fraudsters detail that during the payment process they will notify the user that the name on the credit card statement will be vague and not related to the adult industry in any way, in order to masquerade the transaction. This is another reason why the fraudsters need so many different acquirers.
It’s all these components combined that make the payment processor think it’s a legitimate transaction. Eventually, once [some of] these users find these charges, they will immediately approach the issuer for a dispute and replacement of the card number, which will cause chargeback.
At certain points of this scheme, the fraudsters will reach the maximum available chargeback rate, and the ability to charge more cards will probably be revoked. But by then, they will have already managed to withdraw the funds (most likely to an account owned by a mule) according to their payment conditions. In addition, they will already be on the lookout for the next payment provider to scam.
In Conclusion
As intricate as the setup of this credit card scam is, it nonetheless relies on the naivety of the consumer and the possible unsuspecting payment processors in order to be successful. It’s our job to raise awareness in order to stop these schemes in their tracks, making them inoperable.
We recommend credit card owners check their monthly billing statements and report any suspicious charges as soon as they appear. Neglecting to report an unknown charge, however small it may be, gives threat actors ample opportunity to continue with their schemes.
ReasonLabs has contacted the companies abused by the fraudulent network to help them shut down the operation.
















