Executive Summary
The Metaverse and Virtual Reality (VR) have arrived. What used to be thought of as science fiction has been brought to life in recent years - 171 million people worldwide are using some form of VR today and together the Augmented Reality (AR), Mixed Reality (MR), and VR market size isexpected to reach over $252 billion by 2028. While the market is large and filled with different providers, many users are utilizing Android-powered devices such as Meta’s Oculus and HTC’s Vive. In fact, according to IDC, Meta’s Quest 2 product has nearly 15 million users and its VR sales have grown 242% in Q1 ‘22.
In the enterprise sector, companies dedicated to healthcare, defense, logistics, manufacturing, and more are using proprietary VR apps to train their employees. To install these apps, devices must be switched into Developer Mode. On the consumer side, the move to Developer Mode is required to install free, unofficial, or pirated versions of games and applications. Favored ways for installing free games on VR devices include popular platforms such asSteam, SideQuest, and piracy sites.
ReasonLabs researchers have identified an attack vector that can connect remotely to Android-based VR devices, set to Developer Mode, and record the headset screen.
The attack vector occurs when malware enters a user’s computer, and stays idle on the PC, waiting for a Developer Mode-enabled device to connect to it. Once the malware recognizes a VR device, it begins its actions to enable connection based on WiFi. The malware can then record the user’s headset screen from the PC even without a cable, anytime the device is connected to the same WiFi network as the infected computer until the device is turned off. Recordings can be exfiltrated back to the attacker.
Endpoint Detection (EDR) and Antivirus providers must adapt their systems to provide defense for next-generation threats and improve metaverse security. As such, the new version ofRAV Endpoint Protection prevents malware, including the “Big Brother” threat, from utilizing remote device attacks. It’s equally important for consumers to understand the risks involved in switching their devices to Developer Mode. If Developer Mode is necessary, be sure to take the proper precautions by utilizing next-generation endpoint protection solutions on all personal devices.
Introduction
We noted a rise (or possibility) of programs that are VR-related, which run on end stations. While the VR field is relatively new to us, it has strongly caught our attention. We began to analyze data on executables, APKs, repositories, and forums that are related to the topic. We discovered that there is huge hype around the field of VR and that users are continuously searching for more games, applications, and new ways to do ordinary things using their VR headsets.
The market for VR is continuously developing, with new companies and headsets coming out regularly. Companies developing these headsets include but are not limited to:
- Sony - https://www.playstation.com/ps-vr/
- Valve - https://www.valvesoftware.com/en/index/headset
- HTC - https://www.vive.com/
- HP - https://www.hp.com/us-en/vr/reverb-g2-vr-headset.html
- Meta - https://www.oculus.com/
These VR headsets provide a new way to experience reality, with new games and applications that transport you to a new location. When VR was just in diapers, as with many new inventions, users were concerned about their privacy more than anything.
The developing companies did, and are, going to great efforts to ensure that the headsets and the software they’re running are secure and safe. Those protections are reflected in the code and operating system hardening, and also later in the stage of digesting new applications. All applications that are offered in the app store undergo security scanning and have to meet strict requirements.
For example, it is not at all possible to use the cameras for no reason, and the device is not rooted, so the user does not have many permissions. People are concerned with the privacy of their data, but the usage of cameras and microphones that are part of the headsets shouldn’t be underestimated either.
How VR Headsets Operate
VR headsets come in different shapes, sizes, operating systems, and costs. Some of their operating systems are based on Windows, some on Android, and some require a PC, smartphone, or console. For example, the HP Reverb G2 headset runs on Windows 10 installed on PCs and the PlayStation VRoperates through the PS4 and PS5.
Two major VR providers chose to develop their headsets based on the Android operating system - Meta and HTC. They are using a customized version of Android, so applications and games are in the form of APK files. This means it is also possible to interact with the headset with Android Debug Bridge (ADB) (which we will detail more about below).
How Popular Is The Use Of Developer Mode?
The use of VR headsets in Developer Mode is widespread and becoming increasingly more prevalent, whether it is for use in the enterprise or home entertainment. It’s nearly impossible to determine how many VR headsets are being used in Developer Mode throughout the enterprise world. However, on the consumer side of things, it’s easier to make a determination.
We’ve concluded that millions of VR devices today are currently being used in Developer Mode by consumers around the world. To figure this out, we carefully researched popular forums, websites, online groups, and studied video click counts, views, and publicly available website traffic data.
For example, the popular VR gaming platform SideQuestVR has over 1.2 million unique monthly visitors according to SimilarWeb. Our team also managed to analyze a host of instructional videos on YouTube dedicated to turning VR devices to Developer Mode, which together have almost 2 million views at the time of writing this article. Forums and group chats that provide instructions on Developer Mode are also widely used through channels such as Telegram and Reddit.
Gaming On VR
Gaming is one of the biggest use cases for VR today as expected global revenue from VR gaming will be$2.4 billion by 2024. Games for VR often aren’t cheap, and this is especially true as sometimes users like to buy a few games at once to experiment with the headset and experience all the environment has to offer. This could pose a problem for the younger audience, who are more likely to have limited access to money.
Common ways to get discounted or free games are to search for them on leading platforms such as Steam and SideQuestVR or download them illegally. Pirated games and software in general (outside the VR world) are notorious for delivering malware - according to astudy from the NUS, 34% of downloaded pirated software comes bundled with malware.
Sideloading Games Onto Android-Based VR Devices
In order to install applications outside of the official app store, a user would have to ‘sideload’. Sideloading is the terminology used for loading an external resource on the device. There are a couple of ways to install external games but all of them begin with a tutorial on how to switch the headset to Developer Mode. The move to Developer Mode is essential and cannot be avoided if one wants to perform manual advanced operations.
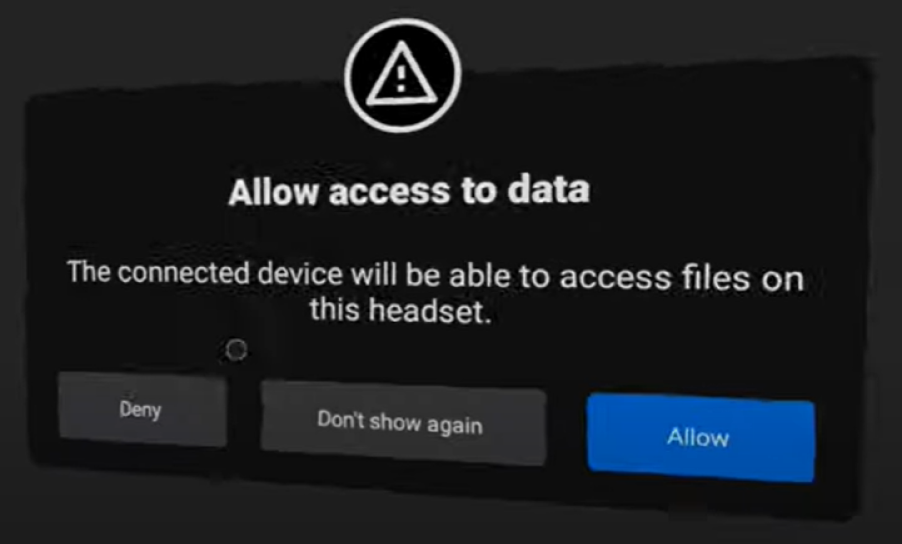
Once Developer Mode is enabled, it is possible to execute commands on the Android device using Android Debug Bridge (ADB) from the computer. Android Debug Bridge is a versatile command-line tool that lets you communicate with a device. The ADB command facilitates a variety of device actions, such as installing and debugging apps and providing access to a Unix shell that you can use to run a variety of commands on a device.
With ADB, it is possible to open a remote connection to install APK files (Android Package files), run them, copy files to and from the device, and more. The external games are APK files, and can be installed from the computer using the command:
adb install application.apk
However, once the device has been switched to Developer Mode, it is possible to do a lot more than just installing applications. Most VR headsets allow you to record the screen by manually clicking on a record button in the Main Menu while wearing the headset. But what happens if a user wants to record the screen from their computer? Based on each headset and its operating system, we can choose an aiding program that will help us record the screen. Using Android-based headsets, we can start screen-recording remotely from the computer by using ADB commands.
https://adbshell.com/commands/adb-shell-screenrecord
We have yet to encounter a malicious VR APK game, but it is possible that a user can download one from an untrusted source. Trusted sources that also perform code validation and developer verification are putting up roadblocks in spreading questionable APKs. One example of a trusted source is SideQuest, which hosts many free original games.
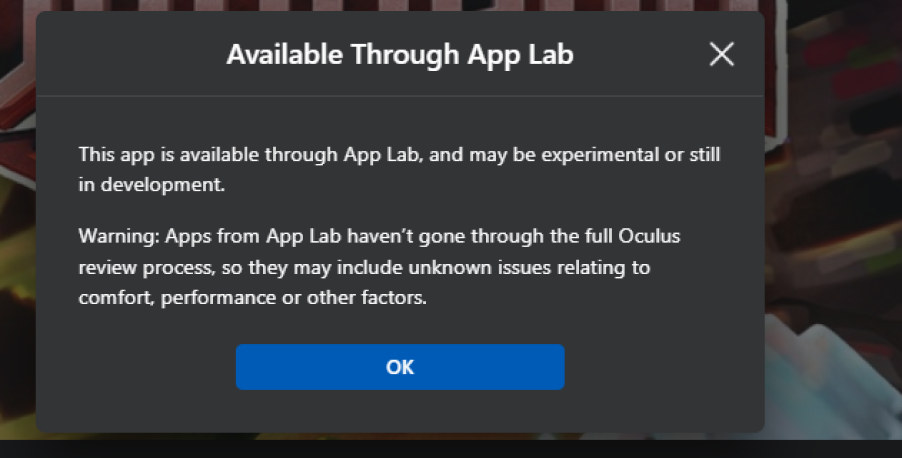
Recently SideQuest also began cooperating with Oculus to directly deliver games to the Oculus Store. They are working closely to enable the discovery ofApp Lab apps on the platform, eliminating the need for sideloading. This initiative is called “AppLab”, and they have clear restrictions on the nature of the APKs that could be uploaded there. However, those apps are still not going through the full Oculus review process, so it might be possible to take advantage of this.
Not All Fun And Games - Proof of Concept (POC)
We wanted to test a scenario where a user switches to Developer Mode on their headset. What could happen to the device after that? The first possibility is that the users think they downloaded a game for VR, and run the program, which is in fact a Trojan. Then the program waits for the users to connect the headset to their computer.
Oculus is extremely popular and also relatively inexpensive compared to some of its peers, which do not require a console or PC in order to operate it. For those reasons, we chose to test this theory on an Oculus Quest 2.
To demonstrate the risk in this scenario, we prepared a POC of such a case, where the user connects the headset to the computer, and at that moment the malicious executable connects to the headset. It then opens a remote port so it can continue its malicious actions even after the user disconnects the headset from the computer and sends screen-recording commands to the headset. In this case, the executable on the compromised computer can wait for an active connection and start recording whatever is seen on the headset screen. Disadvantage: it will work until the headset is turned off.
Another possibility with the same program is to install and even run a malicious APK file so the attacker will no longer depend on the user’s computer or cable connection to run more payloads, like meterpreter reverse shell, back to the attacker and then remotely execute commands on the headset. With ADB commands it’s also possible to uninstall existing applications so another malicious case can be the replacement of an existing benign application, which will be replaced with an additional malicious code to run.
What’s The Risk For Consumers?
An attacker trying to watch our gameplay is a nuisance at best and an invasion of privacy at worst - but this is not the factor that is most at stake. It isn’t just games that run on the headset - there are chat programs, personal information, web surfing, and perhaps the most important element: passthrough mode.
Passthrough mode is what helps the users see their room environment, usually in gray-mode, to be able to walk around the room without falling or bumping into furniture. Until recently, it was not possible for games to make use of this mode but now there is a beta feature that lets developers create games that are based on this mode. That means the game takes place in the user’s room or environment, integrating his reality with the virtual one, otherwise known as Mixed Reality (MR).
Let’s revisit two scenarios:
- A malicious program can record the environment of the user when they take the headset off their head and until the headset turns to idle mode. This is possible because the device turns to passthrough mode, ensuring the user does not bump into items or furniture in their immediate vicinity. When the user is in stationary mode and places the device on a desk or table, it might get outside of the boundaries, thus switching to passthrough mode. In this same scenario, the malicious program can record both the environment and whatever is displayed on the screen of the device.
- Let’s say that the user downloaded an untrusted APK file of a game that relies on the passthrough mode. In this case, when the user starts playing this game, and the malicious program is running in the background, the attacker will have footage of the user’s real environment - the structure, furniture, personal items, and whatever other people might be in it.
The Risks Of Using Pirated Software
Pirated games and software in general (outside the VR world) are notorious for delivering malware. According to astudy from the NUS, 34% of downloaded pirated software comes bundled with malware. So if the user is lucky, they’ll land on an unharmed cracked version and can enjoy the game; alternatively, download a cracked game bundled with a nice piece of malware that will run in the background. Why would it be any different for pirated VR games?
Even though the headsets are hardened and the operations a user can do against them are limited, it is possible to abuse legitimate operations or applications, to carry out malicious actions. Because the Android landscape has existed for a very long time now, there are many tools and programs that help developers or end users do certain operations with their Android devices. One example of such a case is developers taking a screen recording of the device in question, to present the capabilities of the program they’ve built. This can be done with certain commands, or by using tools such as “scrcpy”.
Protecting Metaverse Security
Industry action must be taken to protect against these types of next-generation threats and shore up metaverse security. In this particular case, this is especially crucial from the enterprise perspective, as this type of threat can be used to turn a VR device into a vehicle for corporate espionage. Invaluable intellectual property, trade secrets, and private information are at stake and could be compromised.
From the consumer perspective, although Developer Mode might not be accessed by the everyday user, it is being abused by an ever-growing number of users worldwide. The damage potential is enormous - yet taking protective measures on behalf of users is fairly easy and must be prioritized
















