This report is intended to assist in verifying and mitigating the Spider-Miner malware attack.
Important Notice: Do not accidentally delete something you don’t understand - making changes in the Registry can have serious consequences on your computer. The same goes for deleting files from critical folders. If you are not familiar with these terms you can contact ReasonLabs Customer Support for more help.
Enable ‘File name extensions’
- Open a folder
- On the top of the screen, click on “View”, then tick the checkbox of “File name extensions”
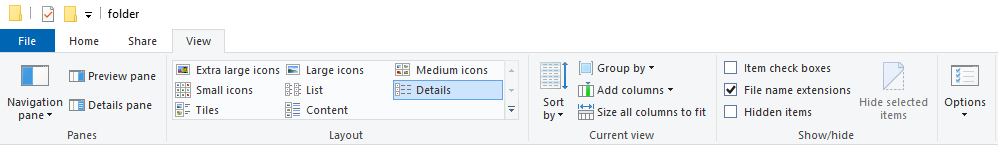
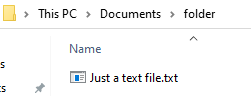
This way, for example, an executable file that claims to be just a text file with extension ‘.txt’ can be revealed.
For example:
Before enabling file name extension:
After:
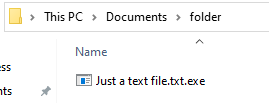
If it was really just a text file, the name should end with ‘.txt’:
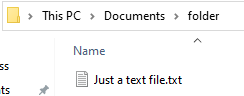
In the Spider-miner case, the file called itself ‘.torrent.exe’. Users that don’t have this setting enabled won’t see the ‘.exe’ extension, and will be tricked into thinking this is a torrent file.
Folder paths indicators of compromise:
*N.B.: These paths can vary, so not having them present does not necessarily mean that the computer is not infected — it is advised to check the rest of the indicators. On the other hand, if you do find those files, it means you have been infected.
To eliminate this threat you must delete those files. If you get an error, it is possible you should first end the running processes and later come back to this step.
In the samples we researched, we found files created at the following paths:
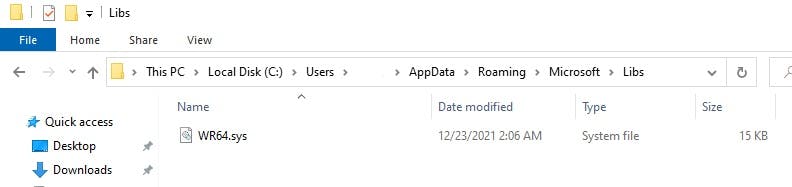
- c:\users\{user}\AppData\Roaming\Microsoft\Libs\WR64.sys
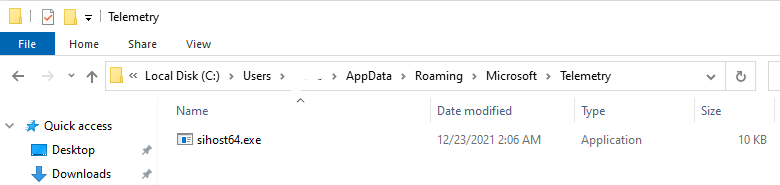
- c:\users\{user}\AppData\Roaming\Microsoft\Telemetry\sihost64.exe
- c:\users\{user}\AppData\Roaming\Microsoft\Services.exe
Removing Persistence Mechanisms
Registry persistence through ‘Run’ key
To check if the persistence key exists, open ‘Registry Editor’ by searching for it in the start menu.
Paste: “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” in the box present under the bar:
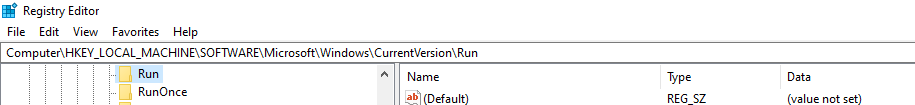
If your machine has been infected with this miner, you will see a key named “Services”, and under Data: “C:\Users\admin\AppData\Roaming\Microsoft\services.exe”
Scheduled tasks
Open ‘Task Scheduler’ by searching for it in the Start Menu.
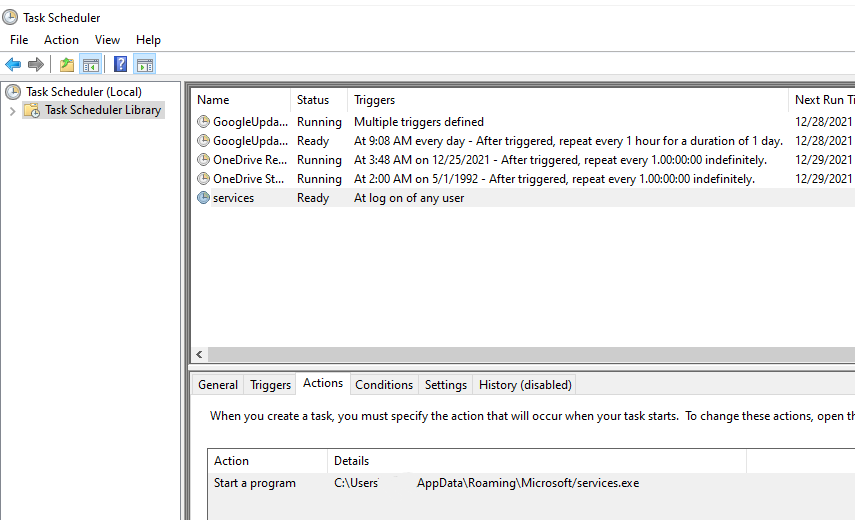
Click on ‘Task Scheduler Library’ and examine the entries on the right.
Search for a task named “Services”. In the“Actions” tab you will see the path: C:\Users\admin\AppData\Roaming\Microsoft\services.exe.
Terminate “watchdog” process
In order to make sure we stop the mining process once and for all, we need to stop the watchdog process that revives the miner if it fails to operate.
Open Task Manager by pressing Ctrl+Shift+Esc on the keyboard.
Click on “Details”.
Right-click on “Name” and click on “Select Columns”
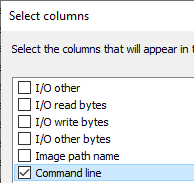
Scroll down until you see ‘Command line’ and tick the checkbox next to it. Click on OK.
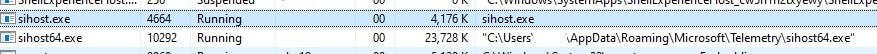
Now search for a process named “sihost64.exe” (or another name, if you had found it in the folder under Microsoft\Telemetry).
Notice there are two instances of sihost running - one of them is an original process of the operating system, and should not be terminated! Please make sure you terminate the correct one by examining the command line — notice the difference between the original one and the malware one (the one that is running from appdata\roaming\microsoft\telemetry folder):
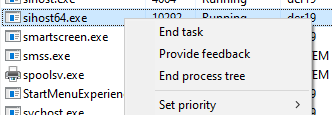
Right-click on the process and click on “End process tree”. This will kill the watchdog.
Terminate mining process
In the same task manager window, search for a process named “svchost.exe” (in some cases we also saw that the miner injects itself to “explorer.exe”, and more).
Between all of the occurrences, search in the Command line column for text that looks somewhat like:
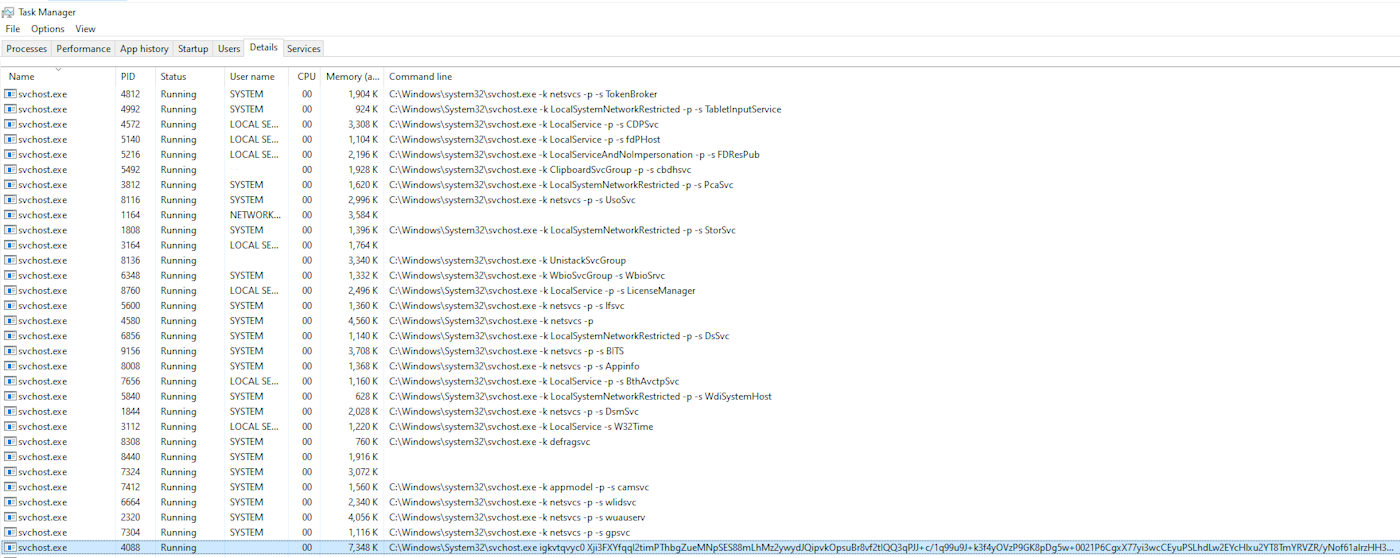
The rogue process can be easily detected by the length of the command line.
The text might be different from this example, but the structure should look like: [processname.exe], space, 10 characters, space, lengthy complex string
If you find these IOCs on your machine:
- first terminate the relevant processes
- then proceed to delete the files from said folders
- and finally, delete the scheduled task / registry key if they exist.
Deleting all of the above will ensure that the threat is removed.
About ReasonLabs:
ReasonLabs is a leading cybersecurity company providing enterprise-grade protection for all users around the globe. Led by a team of cyber experts and visionaries, including former Microsoft Lead Security Program Manager, Andrew Newman, ReasonLabs has developed unique, cutting-edge technology to combat all emerging cyber threats at the earliest possible stage. ReasonLabs' innovative engine scans over 1 billion files in 180 countries a day, delivering fast, comprehensive data, and providing 24/7 real-time threat detection. To learn more about ReasonLabs, please visit https://reasonlabs.com
















